Attacks 
Attacks are groups of attack events that target applications and servers. There are multiple attack events that Contrast includes in an attack, including, but not limited to:
SQL injection
Untrusted deserialization
Command injection
Many other common vulnerability types
When Contrast detects multiple attack events from the same IP address within 60 minutes, Contrast groups these events together as an attack. If Contrast sees new events from the same IP address after you fix the code, Contrast shows a new attack.
The displayed dates on the dashboard for attacks seen are based on the time when the Contrast task runs on the server, not your local timezone.
Event data retention
For on-premises customers, Contrast keeps attack event data for 30 days before removing it. To keep attack data for a longer amount of time, do the following:
A webhook receives data in a POST request only when a specified event occurs. When the webhook sees the event, it collects the data and sends it to the specified URL.
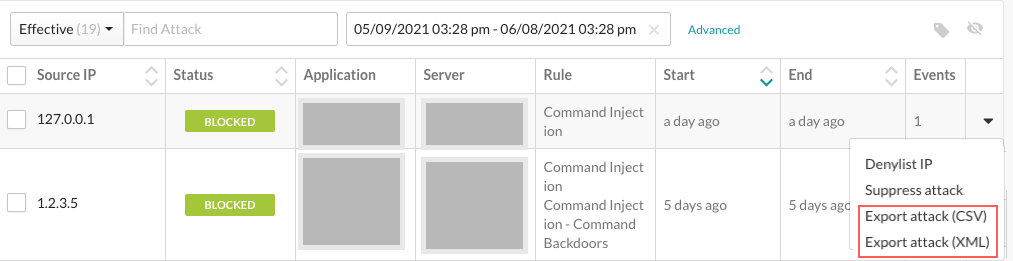
Select the arrow at the end of the attack row and then select Export attack (CSV) or (XML) from the menu.
Exclusion of PROBED event data
You can choose to stop saving data for attack events with a PROBED result. You might want to do this to reduce your database storage consumption for attacks that have a lower likelihood of being problematic.
To stop saving PROBED event data, use this JVM argument in the contrast-server.vmoptions file.
contrast.feature.TS-37298_do_not_save_probed_attack_events=on
This setting applies to all organization in your Contrast instance.
Tasks
In Contrast, you can:
View attack details such as which application and server was attacked and the location in the code where the attack occurred.
Manage attacks by taking actions on attacks and attack events. For example, you can configure a Protect rule for specific attack events.
Monitor attacks in an overview of current and past attacks.