Generic webhooks
Contrast supports a generic webhook integration to receive notifications on any URL that receives POST messages. You can add custom variables to your payload like $ApplicationName and $ServerId when a Contrast event triggers them.
A generic webhook stays connected as long as the receiving end returns any 2XX HTTP response code. If the generic webhook receives too many non-2XX response codes, it disconnects.
Connect
To connect a generic webhook:
Retrieve the URL from which you want Contrast to receive notifications.
In the user menu, select Organization settings > Integrations.
In the Generic webhook integration option, select Connect.
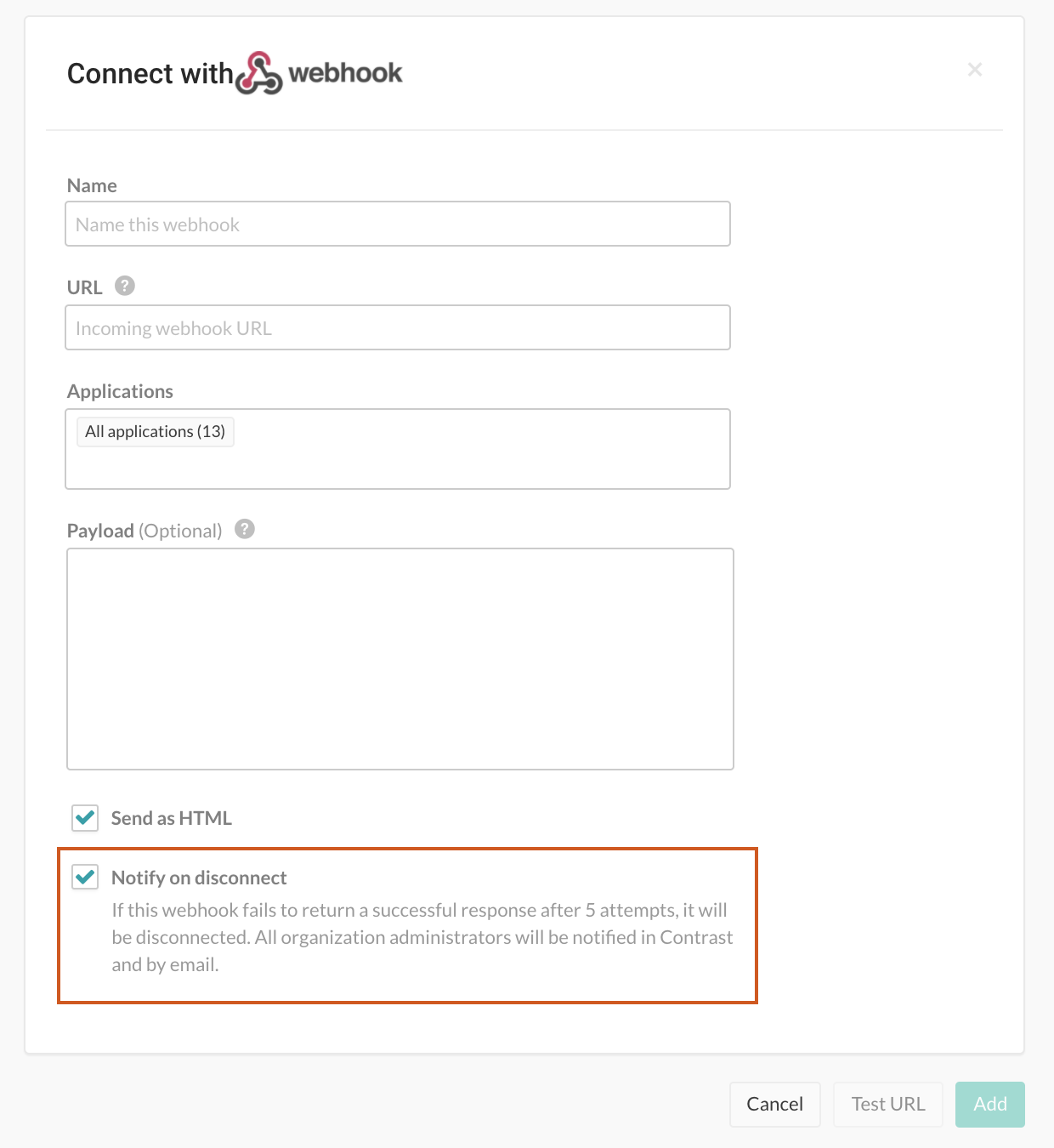
Name the webhook, and paste the URL in the designated field.
Select the application(s) that you want to filter.
In the Payload field, enter a variable. For example:
{ "title": "$Title", "message": "$Message" }Select Add.
To test the webhook:
Go to Organization settings > Notifications.
In the dropdown under Integrations, select the generic webhook name.
For each Subscription (event type) you want to be notified of, click the toggle in the Integrations column.
Cause an event type to occur, and confirm that you get a notification at the URL specified.
Note
If this webhook fails to return a successful response after 5 attempts, it will be disconnected. To restore the configuration, you must retest the connection and resave it.
You can configure the integration so that all Organization Administrators are notified in the Contrast application and by email when Contrast disconnects a generic webhook.
To do this, go to the same location: Organization settings > Integrations > Generic webhook > Show configurations. Select the name of the connection you want to configure. Then select the Notify on disconnect checkbox to receive notifications and click Save.
Generic webhook variables
You can customize your generic webhook response with data from Contrast events such as NEW_VULNERABILITYand SERVER_OFFLINE. Each event contains variables you can call in your payload request. Variables are either for general use or for an application, server or vulnerability.
Variables | Description |
|---|---|
General variables | |
| The event type responsible for triggering the webhook For example: SERVER_OFFLINE |
| A message summarizing the event that triggered the webhook |
| The unique ID Contrast assigns to an organization when it is created |
| The name of your organization |
| Always returns “Contrast Security” |
Application variables | |
| Returns true if the application is a child application, false if not |
| A secondary shorthand that appears in the title of an application, and is blank by default For example: TEST |
| The context path of the application For example: |
| When the application was first seen, in Unix time For example: 1572033840000 |
| Returns true if the application has a parent, false if not |
| Enumerated value of the application Importance level For example: MEDIUM |
| The unique ID Contrast assigns to an application when it is created For example: 49fe2978-1833-4441-83db-2b7o486d9413 |
| The importance level assigned to the application For example: Medium |
| The programming language of the application |
| When the application was last seen, in Unix time For example: 1572033840000 |
| Whether or not the application has an Assess license Values: Licensed, Unlicensed |
| Returns true if the application is a primary application, false if not |
| The name of the application |
| The unique ID Contrast assigns to an application when it’s created, in this case, the parent application, if it exists For example: 49fe2978-1833-4441-83db-2b7o486d9413 |
| A comma separated list of the Application tags. |
| The number of modules your application has |
Server variables | |
| The environment of the server For example: DEVELOPMENT or PRODUCTION |
| The ID of the server involved in the event If more than one server is involved, this is a comma-delimited list of server IDs. |
| The name of the server involved in the event If more than one server is involved, this is a comma-delimited list of server names |
Vulnerability variables | |
| If this event is triggered by a vulnerability, this is the severity of the vulnerability |
| If this event is triggered by a vulnerability, this is the status of the vulnerability |
| If this event is triggered by a vulnerability, this is the vulnerability ID |
| The application language or framework name of the where the vulnerability was discovered (for example,.Java, .NET, Ruby, and so forth.) |
| The application versions the vulnerability is found in For example: v1.2.3 |
| Auto-remediated expiration period for the vulnerability, in Unix time For example: 1572033840000 |
| A comma delimited list of tickets created when the vulnerability was sent to bugtracker For example: ticket1, ticket2, ticket3 |
| The category of vulnerability found For example: Injection |
| When the vulnerability was closed, in Unix time For example: 1572033840000 |
| Confidence of the vulnerability |
| Default severity of the vulnerability |
| When the vulnerability was first discovered, in Unix time For example: 1572033840000 |
| The evidence of the vulnerability |
| The unique ID Contrast assigns to a vulnerability instance when it is created For example: R33T-N00B-TGIF-RM6P |
| When the vulnerability was first seen, in Unix time For example: 1572033840000 |
| The impact level of the vulnerability Values: Low, Medium, High |
| Last time the vulnerability was seen, in Unix time For example: 1572033840000 |
| Last time the vulnerability was seen, in Unix time For example: 1572033840000 |
| License level of the vulnerability |
| The likelihood of the vulnerability Values: Low, Medium, High |
| When the vulnerability was sent to a bugtracker, in Unix time For example: 1572033840000 |
| Returns true If the vulnerability was sent to a bugtracker |
| Rule associated with the vulnerability |
| Name of the rule associated to the vulnerability |
| Title of the rule associated to the vulnerability |
| Substatus of the vulnerability |
| Custom tags associated with the vulnerability For example: my-custom-tag |
| Title of the vulnerability |
| Key code of the vulnerability substatus |
| Total number of times the vulnerability was received |
| The unique ID used to look up a vulnerability |
| true if the vulnerability is licensed and visible, false if not |
| If event is triggered by a vulnerability, this is the rule that the vulnerability violated |
| If event is triggered by a vulnerability, this is a comma-delimited list of tags associated with the vulnerability |
Events and generic webhook variables
You can customize your generic webhook response with data from Contrast events such as NEW_VULNERABILITY and SERVER_OFFLINE. Each event contains general, application, server or vulnerability variables you can call in your payload request.
Event | Variables |
|---|---|
| |
| |
| |
| |
| General, Application and Server (if new application) |
| |
| |
| |
| |
| |
| |
| |
| |
| |
|