Send output to syslog
Contrast lets you send security logs to a remote syslog server in addition to the Contrast Security log. Syslog message format describes the components in the messages that Contrast sends.
Before you begin
You must apply a Protect license to the server that has syslog output enabled.
You may have to enable remote logging so that your syslog can receive outside messages.
Syslog messages for a server are sent by the agent.
Syslog output isn't supported over TCP.
Steps
When configuring the default organization server settings, select the checkbox to Enable output of Protect events to syslog, which reveals additional fields, and then enter the appropriate settings.
Select Servers in the header to enable and configure syslog output to an individual server or multiple servers at one time. If syslog defaults have already been set at an organization level, the values will be pre-populated for server-level settings.
Individual server: To enable syslog on an individual server, hover over the grid row, and select the Server settings icon.
Multiple servers: Use the check marks to select multiple servers, and select the Server Settings icon in the batch action menu that appears at the bottom of the page.
Note
If one or more of the selected servers is not eligible to have syslog enabled, it will only be enabled on eligible servers.
In the Server settings window, select the box to Send output of Protect events to syslog. (For multiple servers, you will need to select Edit next to the checkbox first).
Note
If eligible servers selected are in different environments, you can choose to use the default settings for the applicable servers or manually configure the settings for all servers.
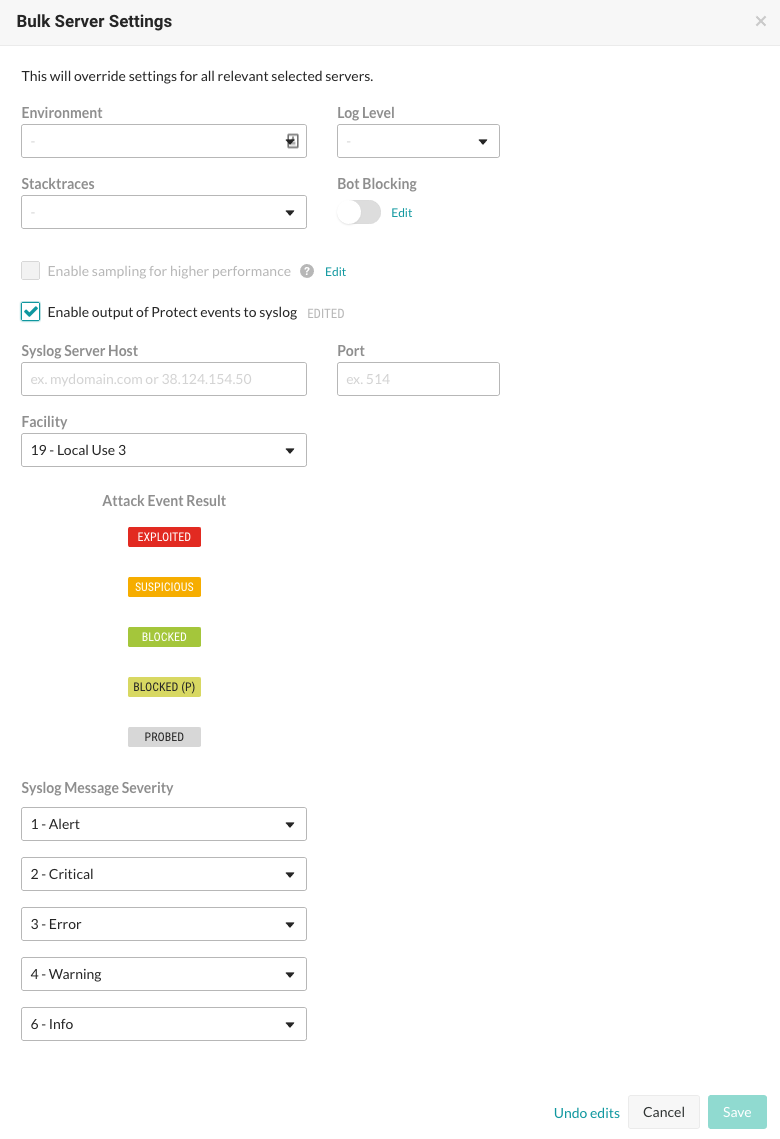
Enter the Syslog server host. This can be the full qualified domain name (not just the hostname) or the IP address. For example: email.mydomainname.com or 38.124.154.50.
Enter the Port.
Enter the Facility.
Enter the Syslog message severity.
Save the settings to enable syslog on the server.
When syslog is enabled, the server has a gray arrow icon beside its name in the grid. Hover over the icon to see the output location of Protect events.
To edit server settings, repeat the steps above to update the values in the appropriate configuration form, and save your changes.
Syslog message format
Syslog messages are formatted using the Common Event Format (CEF), a standard format that most Security Information and Event Management (SIEM) solutions use to facilitate the parsing and analysis of log data.
The following example shows the format that Contrast uses for syslog messages that it sends:
Aug 04 2024 192.168.219.65 CEF:0|Contrast Security|Contrast Agent Java|4.5.2.0|SECURITY|The parameter undefined2 had a value that was marked suspicious reflected -xss - <script>alert('TURTLES-everywhere')</script>|WARN|pri=reflected-xss src=10.80.49.96 spt=8443 request=/actuator/info requestMethod=GET app=svc-basic outcome=SUSPICIOUS dvchost=my.example.hostname.com computer=my.example.hostname.com contrastAgentServer=my-server-name from contrast.yamlThe components in the Contrast syslog message are:
Date: The timestamp of the local host indicating when the log was generated. For example:
Aug 04 2024.The timestamp uses this format:
MMM dd HH:mm:ss, which shows the current time zone of the server running the agent.Host: The host address where the log was generated. For example:
192.168.219.65.CEF Version: The version of the CEF format being used. For example:
CEF:0.Device Vendor: The vendor of the security device. For example:
Contrast Security.Device Product: The product that is generating the log. For example:
Contrast Agent Java.Device Version: The version of the product generating the log. For example:
4.5.2.0.Signature ID: The type of event. For example,
SECURITYindicates a security-related event.Message: A description of the event. For example:
The parameter undefined2 had a value that was marked suspicious reflected -xss -<script>alert('TURTLES-everywhere')</script>.Log level: The log level of the event. For example,
WARNorDEBUG.Extensions: Other fields that provide further details about the event. Some examples include:
pri: Priority of the event.src: Source IP address of the event.spt: Source port.request: The specific request that triggered the event.requestMethod: The HTTP method used.app: The application involved in the event.outcome: The outcome of the event (for example, Suspicious or Blocked).dvchost: The hostname of the machine where the event occurred.contrastAgentServer: The value of thecontrast.server.nameproperty or the host name as a fallback.
Syslog receivers
When you configure receivers for syslog output, consider these resources: