Configure LDAP
Contrast integrates with many types of Lightweight Directory Access Protocol (LDAP) servers. LDAP is an Internet protocol that web applications can use to look up users or groups listed on an LDAP directory server.
Contrast supports these LDAP server types:
OpenLDAP
OpenDS
ApacheDS
Fedora Directory Server
Microsoft Active Directory
Generic LDAP Servers
Connecting to an LDAP directory server is useful if you manage users and groups in a corporate directory, and you want to delegate the responsibility of managing user access of the application to your corporate directory administrators.
Note
Switching to LDAP from a different authentication method such as a local database may result in issues if the user ID attribute is inconsistent.
A system administrator can configure the LDAP server:
Important
If you configure your LDAP integration to connect to your server using SSL, you may need to take extra steps for self-signed or privately signed certificates.
Access if LDAP is offline
In the event that your LDAP service experiences connectivity or configuration issues, use the default SuperAdmin account to log in to Contrast. This feature ensures that you continue to have immediate access to your Contrast account even when LDAP is offline.
Steps
Start by creating a user in the LDAP Server that is a dedicated read-only user or read-write user (depending on how you configure Contrast to interact with the LDAP directory). The user should be have read permission to the directory, including users with permission limited only to the Search Base. You will need this user to set the Search Base when configuring users for LDAP and when binding to user.
Create user groups in the external LDAP server. You will later use these groups to assign SuperAdmin privileges in Contrast.
Under system settings, select Authentication.
Select Change authentication method.
Select LDAP.
Enter required information under Connect server and Bind server.
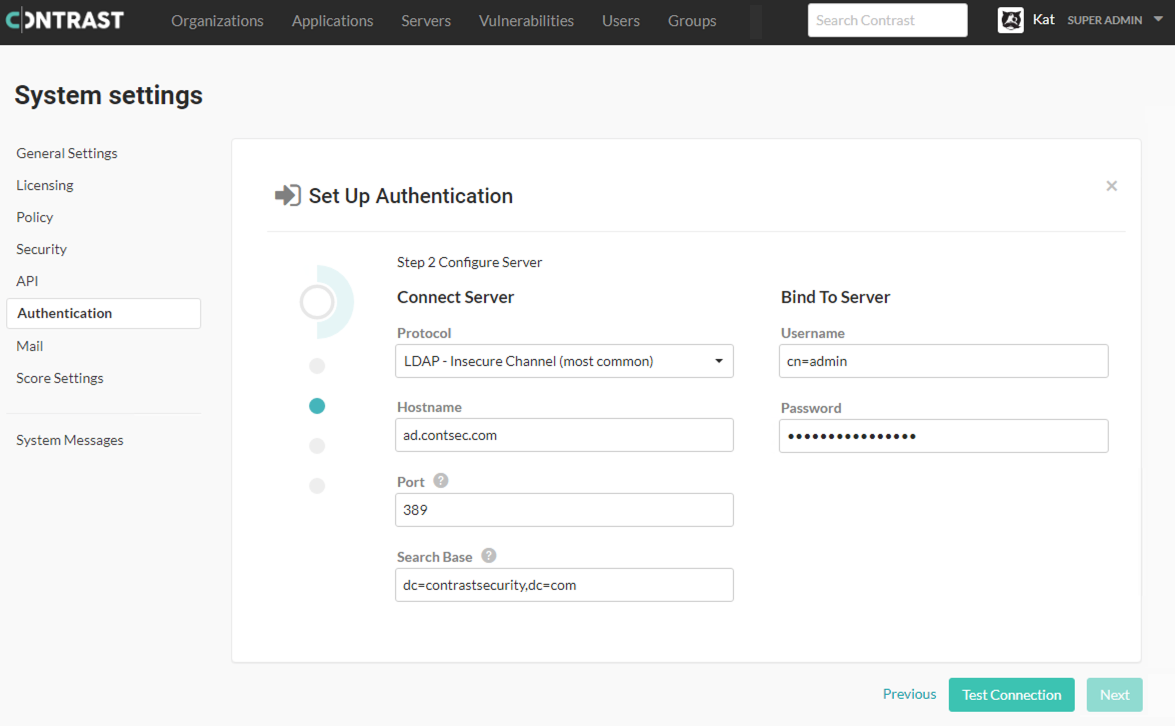
Option
Description
Default
Connect server
Protocol
The protocol that should be used to communicate with the LDAP server. Choose between LDAP or LDAP with SSL (LDAPS).
LDAP
Hostname
Enter the hostname to use when communicating with the LDAP server.
localhostPort
Enter the port to use when communicating with the LDAP server.
389 (LDAP), 636 (LDAPS)
Search base
Enter the base distinguished name (DN) to use when communicating with the LDAP server. If your login domain is yourdoman.com, your base DN would be
dc=yourdomain,dc=com.dc=contrastsecurity,dc=comBind to server
Method
Select the method to use when connecting to the LDAP server. Options are shown in the next table.
Simple
Username
Enter the full DN of the user that should bind to the directory to perform queries and check authentication.
N/A
Password
Enter the password for the bind user specified in the Username field.
N/A
There are four supported bind mechanisms that can be used by Contrast. Each has different required fields:
Method
Description
Required Fields
Optional Fields
Anonymous
Administrators provide anonymous, read-only access to the directory.
None
N/A
Simple
This is standard username and password authentication. The username and password are verified as provided by the LDAP server.
Username, Password
N/A
DIGEST-MD5
A username and password are provided and hashed using MD5 prior to sending to the server to be authenticated.
Username, Password
SASL Realm
CRAM-MD5
The LDAP server issues a pre-authentication challege, which is sent with the MD5 hashed username and password to be authenticated.
Username, Password
SASL Realm
Once you configure the connection to the LDAP server, select Test connection. Testing the connection ensures that the application can connect to the LDAP server and perform queries.
To verify that the group and user mappings are correctly configured, select Test login.
Once you've successfully logged in as both SuperAdmin and Organization Administrator, select Finish to complete the configuration.