Configure groups for LDAP
As part of the LDAP configuration, you will need to configure groups.
Organization Administrators set the roles and permissions for users, and each application handles roles and access to data within that application. When configuring users, you can opt to add users to an access group on login. However, even if that is not enabled, Contrast uses the LDAP directory to ensure that the provided user belongs to the correct group.
To configure groups:
Enter the following values:
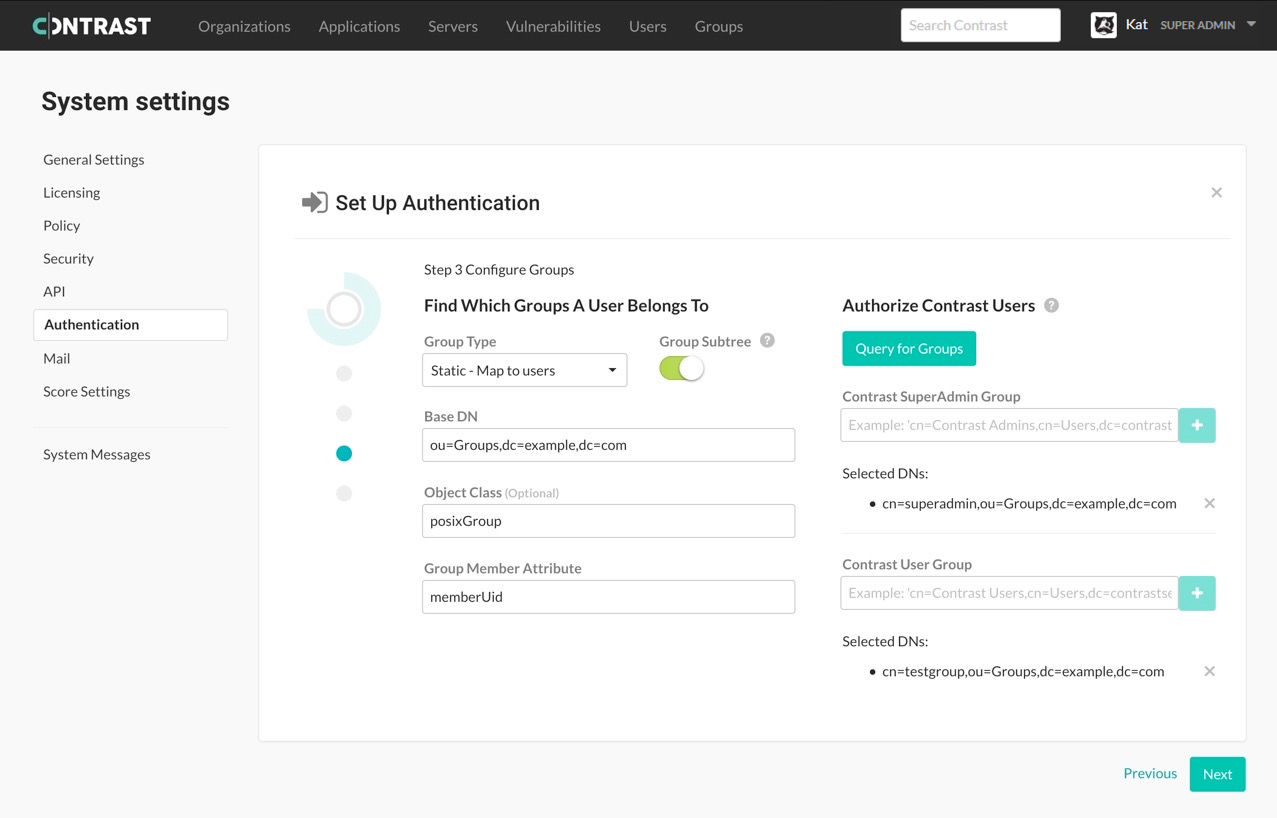
Option
Description
Default
Group type
Groups types depend on your server functionality and configuration. Groups are either:
Static: Groups track members through an attribute on the object, such as
uniqueMember. The remaining four options in this table only apply to static groups.
Dynamic: The user object tracks its own membership. Groups are added dynamically to the user object when the user becomes a member of a group.
Static
Group subtree
Configures whether subtrees of the Base DN should be included when searching for groups in the directory.
Enabled
Base DN
This is the distinguished name (DN) where the application can find groups in your LDAP server (like the User Base DN).
ou=GroupsObject class
If left blank, the application uses the default values of "
group," "groupOfUsers," or "groupOfUniqueUsers." This isn't a required field, as it is standard across LDAP deployments.N/A
Group member attribute
The attribute within a group object in the directory that contains the members of that group. This may differ for your LDAP deployment, so ensure that you are using the correct attribute with your LDAP administrator.
Each member of the group should be listed as a full distinguished name (DN) not a relative distinguished name (RDN). For example: "cn=smith,ou=Users,cn=support,dc=test,dc=org").
If you use an RDN, Contrast does not see that user in the LDAP group.
uniqueMemberUse the groups you previously created in your external LDAP server, to assign users to one of the following groups
SuperAdmin group: This group allows users to log in with SuperAdmin permissions.
Users group: This group allows users to be added to an organization and log in to the standard interface. This group is appropriate for all other users.
Important
If a user belongs to both groups, and provisioning is disabled, the user will be created as a SuperAdmin. If provisioning is enabled, the user will be created without SuperAdmin permissions.
Select Query for groups to enable a live search of existing groups as you begin to type within the input fields.