Configure users for LDAP
As part of the LDAP configuration, you will need to configure users.
To fully integrate with an LDAP directory, Contrast needs information on how to connect to the LDAP server as well as how to find users and groups within the directory.
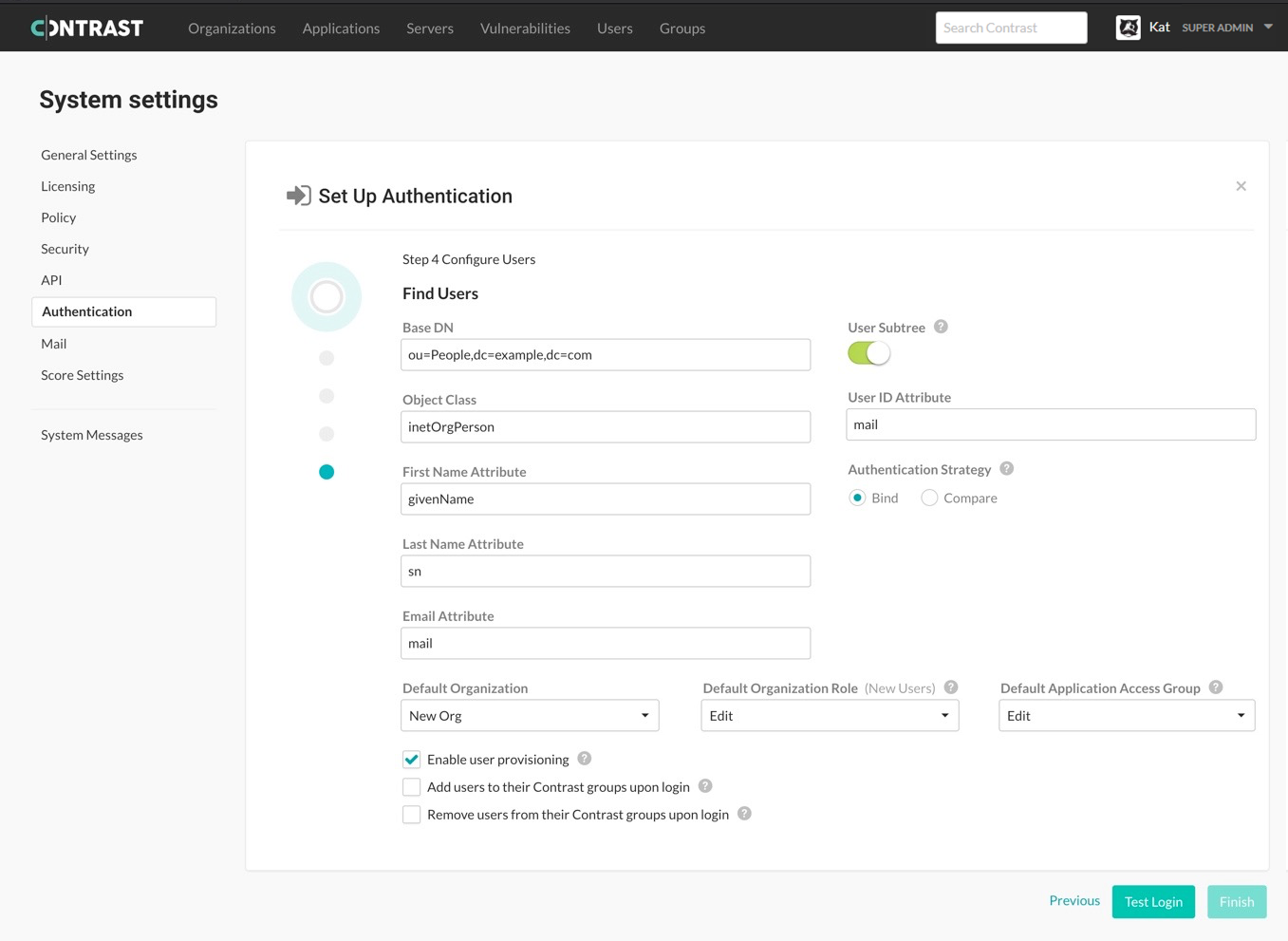
Enter the following information on how you want Contrast to search for users in the directory. The default settings are correct for most LDAP deployments.
Option
Description
Default
Base DN
Indicate the container (under the global base DN) where Contrast should start searching for users. In most organizations, this is a single container (for example, ou=Users), but your LDAP administrator should verify that you're searching the right container.
ou=usersObject Class
Indicate the LDAP object class for user objects in the directory.
inetOrgPersonFirst Name Attribute
Indicate the LDAP field that contains a user's first name.
givenNameLast Name Attribute
Indicate the LDAP field that contains a user's last name.
snEmail Attribute
Indicate the LDAP field that contains a user's email address.
mailUser subtree
If enabled, subtrees of the Base DN are included when searching for users.
Enabled
User ID attribute
Indicate the LDAP field that should be identified as the User ID. This is the username to enter when logging in to contrast.
uidAuthentication strategy
Choose how you want Contrast to authenticate users when they provide their credentials. Bind means the application sends the user's credentials to the server for authentication. Compare means the server hashes the user's credentials and compares them to the value of the password attribute.
Bind
Password attribute
The LDAP field that contains a user's password.
If you selected Compare for the authentication strategy, this attribute contains the hashed password for the user.
userPasswordTo automatically create new user accounts when someone makes an LDAP request to log in, check the box next to Enable user provisioning.
Use the dropdowns to choose the Default organization, Default organization role and Default application access group for the new users.
Contrast can automatically provision or de-provision users at login time based upon the user’s LDAP groups. When this feature is enabled for LDAP-based authentication, users are added to a Contrast access group that maps to a corresponding LDAP group and removed from disallowed Contrast groups. Users can be added to multiple groups, as well as added to groups that give them access to multiple organizations.
Important
For this to work, the Contrast groups must already exist, and the groups from LDAP (for provisioning purposes) must have the same name as the Contrast groups.
To add users to their groups when they log in to Contrast, check the box next to Add users to their Contrast groups upon login. To remove users from their groups when they log in to Contrast, check the box next to Remove users from their Contrast groups upon login.