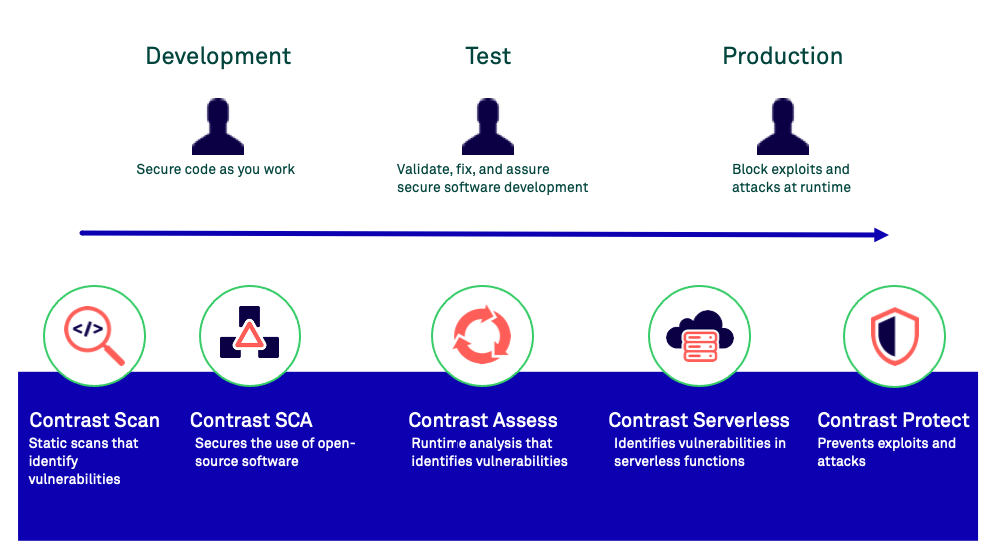
How Contrast works
Contrast Security provides accurate, continuous, real-time application security testing and attack blocking for your application portfolio. Contrast works within each application to secure it across the entire software development life cycle (SDLC).
Contrast transforms functional tests into security tests, so that you get security feedback every time you exercise your applications through your quality assurance function. Contrast delivers results continuously and in real time, so you are integrating security into your entire development pipeline from source code to running applications, and all points in between.
How Contrast integrates with your development environment
Analysis techniques and data sources
Contrast combines numerous data sources and a variety of analysis techniques including:
Runtime control flow and dataflow (IAST)
Application code or APIs (SAST)
HTTP requests and responses
All libraries and frameworks in the application and how they are used (SCA)
Configuration information
Back-end connections
Static scans of local files (SAST)
Contrast agents
Contrast Assess and Contrast Protect use agents to analyze data flow and identify vulnerabilities in fully-assembled and running applications. Contrast Assess and Contrast Protect use the same agent to analyze data flow and identify vulnerabilities in fully-assembled and running applications. You do not need one agent for Assess and another for Protect.
Adding and configuring an agent inserts Contrast code in the application’s existing methods across custom code and libraries. Sensors in the agents observe the locations where data enters and leaves the application (routes). This action creates real-time visibility into any data that flows through the application and allows Contrast to detect security flaws or vulnerabilities in this code path and report them to Contrast. The agents also allow Contrast to identify and block attacks.
Agent configuration
Configuring an agent consists of editing a YAML configuration file, using environment variables on a command line, or other methods native to the language and tools you are using.
When you configure an agent for an application, you specify information for the following settings:
Agent communication with Contrast
Agent-specific settings
Settings for Assess and Protect rules
Application-specific settings
These settings include session and application metadata that are available to you as additional information for each vulnerability reported or as a way to filter them.
The server hosting the application and the agent:
Developer's local application server running in the integrated development environment (IDE)
Continuous integration application server that's used during the automated testing process
Application test server
Application staging server
Embedded server in an appliance
Application server running in a virtual machine
Remote application server running in the cloud
Production application server
Static scans
Contrast Scan is a static application security testing (SAST) tool that makes it easy for you to find and remediate vulnerabilities during the development phase of software development lifecycle (SDLC).
To scan applications, you upload a source code or bytecode file. Contrast technology identifies vulnerabilities based on a set of rules that Contrast defines for you.
Protection for cloud-native applications
Contrast Serverless Application Security is a next-generation application security testing solution for serverless-based applications.
Contrast Serverless Application Security uses cloud-native architecture to map all resources within your environment, while automatically validating and prioritizing the results, eliminating false-positive results and alert fatigue. It uses a ReadOnly access to your AWS account to continuously monitor the environment and collect relevant information.
Integrations
Contrast works with several different integrations to provide accurate security feedback with tools you are already using. This approach accelerates the software development process by encouraging security and development to work together effectively.