Serverless Application Security
Contrast Serverless Application Security is a next-generation application security testing solution for serverless-based applications.
Contrast Serverless Application Security uses cloud-native architecture to map all resources within your environment, while automatically validating and prioritizing the results, eliminating false-positive results and alert fatigue. It scans for vulnerabilities in your custom code (for example, injection attacks), dependencies (for example, CVEs), and configuration risks (over-permissive function policies).
Features
Easy connection to AWS
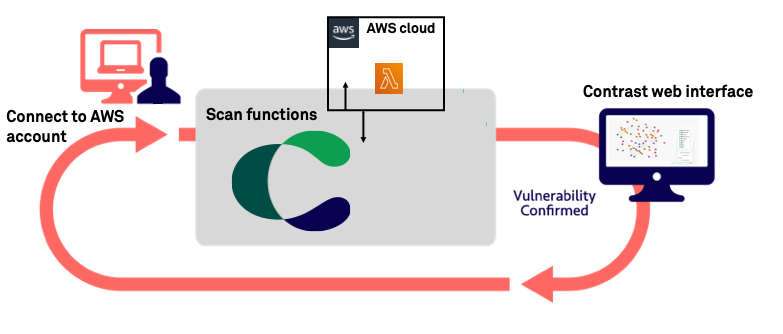
With two clicks and approximately two minutes, you connect to your AWS account through the Contrast web application.
Discovery of your inventory
Once you connect to your AWS account, Contrast creates an inventory of your functions, resources, policies, and services in your AWS environment.
Analysis of vulnerabilities
Dynamic and static scans analyze your code, discovering weaknesses, data flows, attack surfaces, and exposure to vulnerabilities.
Continuous monitoring
As your code changes, Contrast continues to monitor your Lambda functions, identifying vulnerabilities that require attention.
Simulation of attacks
A dynamic scan generates and executes curated attacks on resources and data flows, without making changes to your code.
Visual representation of function and service relationships
In addition to viewing relationships between functions and services in your account, you can view details about each element including applicable risks.
Reporting
Scan results list CVEs, permission violations, vulnerabilities, and other exposures in your code.
Benefits
Fast and easy deployment
You do not need a large staff of specialists or consultants or a lot of time to integrate with Contrast.
Non-intrusive integration
You can add serverless security without significant changes to the development process. It's easy to find and fix exploitable vulnerabilities early in the development phase, ensuring that your applications are more secure when you deploy them to production.
How it works
Contrast connects to your AWS account with ReadOnly access. It uses this access to continuously monitor the environment and collect relevant information.
Contrast deploys one Lambda function (Cloud Agent) within the monitored environment, to perform activities such as code analysis and sending back to Contrast meta-data about the scanned resources (Lambda functions).
All the information is used by our contextual engine to build a tailored attack profile for every resource and change to this environment. The attack simulations will be executed, inside the customer’s account, by the Cloud Agent.
All finding results will go through an internal validation mechanism to qualify them, providing zero false-positive and real prioritized results.
Security and privacy
Contrast does not collect code or code-snippets from your monitored account. Contrast only sends back meta-data information such as:
Identified vulnerabilities
Function names and metadata (for example, policy handlers)
Used libraries
AWS API calls (for example, boto3 and asw-sdk)
Service configurations (for example, bucket notifications, API gateway paths, and methods)
Contrast makes no changes to your code. However, during the scan time (for example, when a function is deployed or modified), Contrast temporarily instruments a layer into the scanned function and makes some configuration changes (for example, timeouts or handlers).
Once the scan completes, Contrast restores the layer and the configurations to their original states. This process is completely transparent and occurs automatically.
During a scan, you can continue to run your own tests (function calls).
During dynamic scans, Contrast executes with scanned function using malicious data. This process has no effect on your code. It does, however, execute code that could potentially trigger any action that the function makes.
This function is disabled by default. Use the Settings tab to enable it at any time.
All data that Contrast receives from the monitored AWS account is encrypted in transit and at rest.
Contrast uses Amazon EventBridge with a shared secret to send and receive all data. There are no web or REST APIs that Contrast uses to communicate with your AWS account.
Requested permissions
When you use Contrast to connect to your AWS account, you consent to these access permissions:
ReadOnlyAccess from the Contrast AWS account to your monitored AWS account.
This policy is used during beta activities only.
Lambda Read/Write access from the Contrast AWS account to the Lambda functions deployed in your AWS account.
The Lambda function that Contrast installs in your monitored AWS account requires these access policies:
Read CloudWatch Logs
Read Layer versions
Invoke function
Change function configuration
Write EventBus messages
Read KMS keys
Read/Write objects to specific S3 buckets (Contrast creates these buckets)