View results
View results to see details about vulnerabilities for permissions, dependencies, exploits, and CVEs.
Ensure that at least one scan is complete.
Select Serverless in the header.
To view results for all scans, select Results. See Scan status details for more information about the meaning of the scan results.
To filter results in the Results tab, select the Filter icon (
 ) next to the column headers.
) next to the column headers.The Severity is based on vulnerabilities in the application. See the Application scoring guide for information about the levels.
The Category is based on vulnerabilities in the type of function.
The Function is based on the function found in your account.
Note that results can also be grouped by Category or Function by selecting the option under Group results on the upper-right side of the screen.
The Source is based on the platform providing the results. It is either from Contrast or AWS Inspector. Click the icon to view details about the results. Note that AWS Inspector results will display only if you have AWS Inspector support for your accounts.
To clear the filters, select the green Filter icon (
 ) icon next to the column headers and select Reset in the filter window.
) icon next to the column headers and select Reset in the filter window.To search for a function in the Results tab, type a search term in the search field.
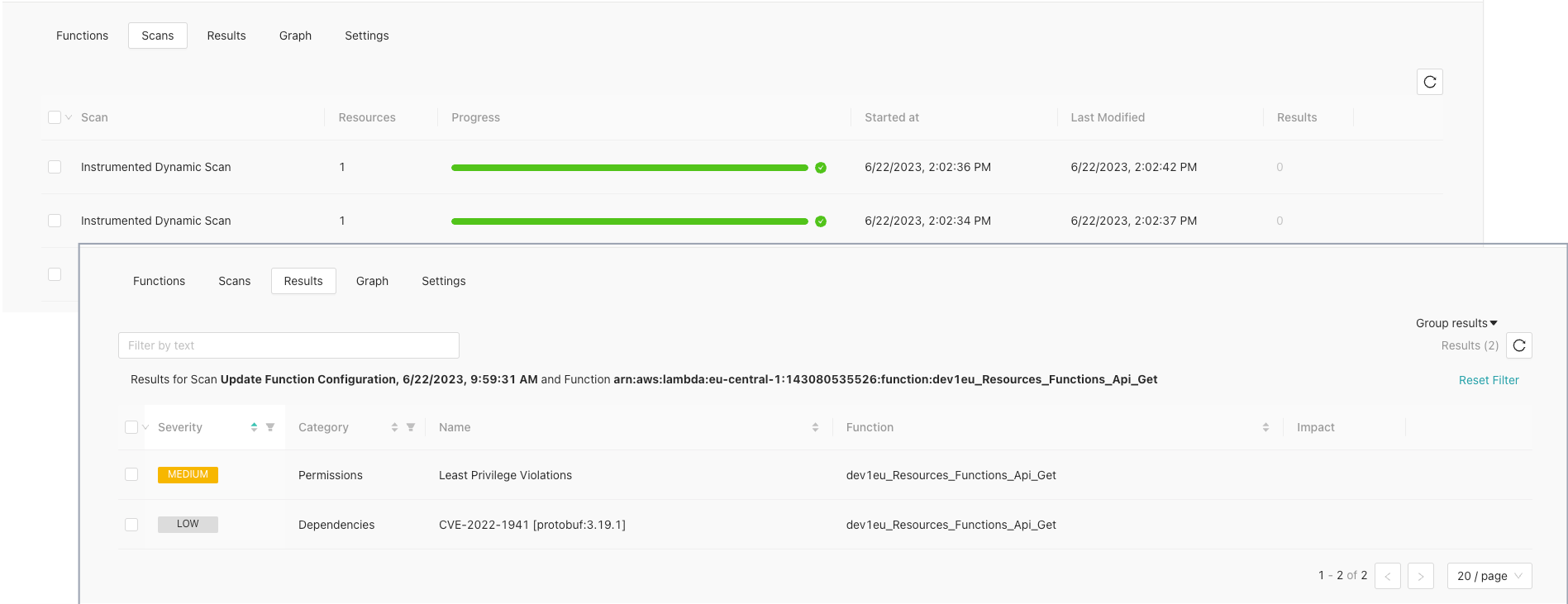
To view results for a single scan, from the Scans tab, select a scan row.
This action shows a scan details page.
To view result details for a function:
From the Results tab, select a row in the list.
From the scan details page, select a number in the Results column for a function.
The results detail page looks similar to this example:
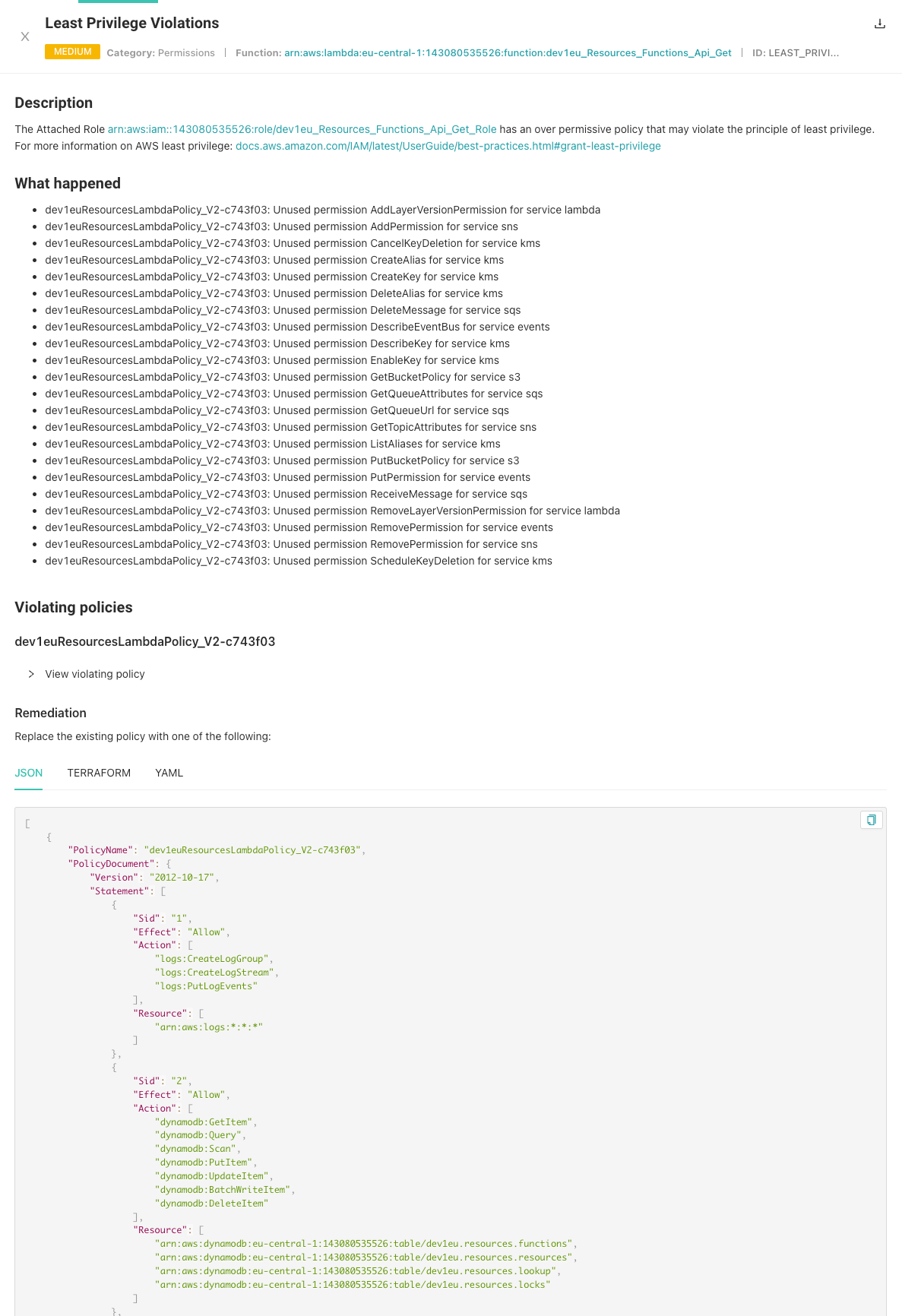
Result details
The result details displayed here depend on the category of a vulnerability.
All results include this information:
Description: A description of the vulnerability.
What happened: What occurred when the scan discovered the vulnerability
Remediation: Steps to take to fix the vulnerability.
You might also see these details:
Violated policies: Policies that the vulnerability violates.
Impact: The area that the vulnerability affects, for example ses, s3, logs, or dynamodb.
Severity and metrics: A severity score calculated to the vulnerability as well as metrics for the areas that the vulnerability impacts.