View attack events 
An attack event occurs when there is a violation of Protect rules or other suspicious application activity in instrumented applications.
Before you begin
If role based access control is turned on, you need a role with the View Attack Data action. Contact Contrast support for access to this action.
Steps
Select Attack events in the header.
Set the main view by selecting an option in Group by:
If you want to view groups of attack events, select a group type (currently the only option is Source IP).
For example, if a source IP address of 111.111.111.111 has multiple attack events, grouping by Source IP displays an aggregated view for all the events.
Group by Source IP is the default selection.
If you want to view all individual attack events, clear the group by selection by moving your cursor to the Group by box and selecting the Delete (
) icon.
To refine the view, open the filter panel by selecting Open filters.
Use any of these filters:
Date range: Select a date range or select Custom to specify a preferred data range.
The default date range is 12 hours.
Severity: Select one or more vulnerability severity levels.
Results: Select one or more result types for an attack event.
Rules: Select one or more of the Protect rules associated with the attack event.
Application: Select one or more of the available applications.
Environments: Select one or more server environments.
Source IP: Select one or more source IP addresses associated with the attack event.
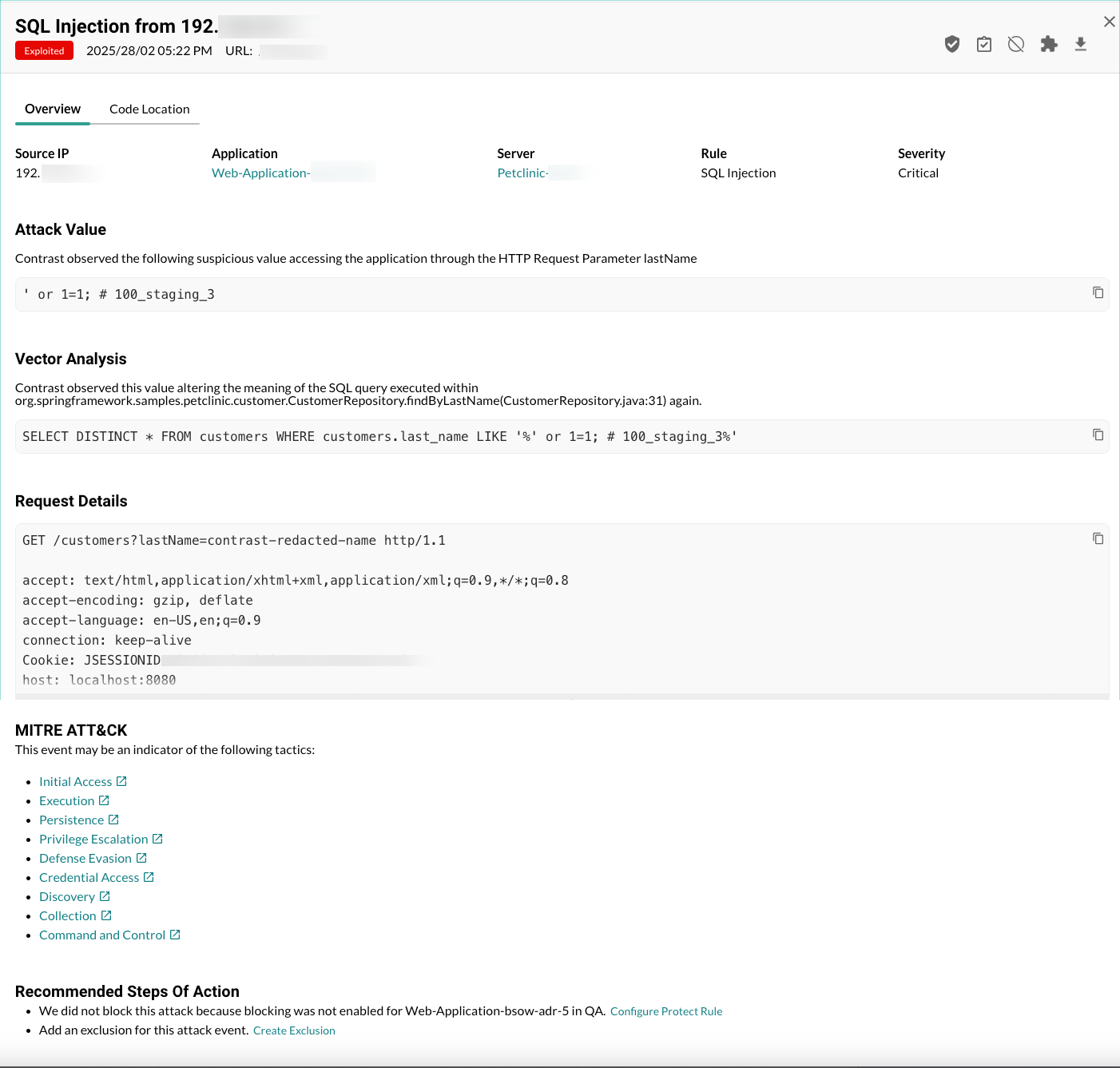
To view details about a specific attack event, select an individual attack event (not a group) which opens the Attack details view. This view includes:
Overview tab: An overview of the attack event details, including these details:
Source IP: The IP address where the attack event originated.
Application: The application affected by the attack event.
Server: The server associated with the application.
Rule: The Contrast rule associated with the attack event.
Severity: The severity that Contrast assigned to the attack event.
Attack value: The suspicious value that Contrast observed.
Vector analysis: The different pathways or methods that Contrast observed where a malicious attacker could gain access to your system.
Request details: The details that Contrast observed in a request associated with the attack event.
MITRE ATT&CK tactics: Links to details for MITRE ATT&CK tactics.
The MITRE ATT&CK framework is a knowledge base of adversary tactics and techniques derived from real-world observations.
A single attack event can map to multiple tactics. In the case where multi-stage attacks events occur, an observed event might represent a single action within a larger attack chain. Alternatively, it could indicate a threat vector.
Combining event data with context from other security tools, such as Web Application Firewalls (WAFs) or Endpoint Detection and Response (EDR) solutions, allows for more precise identification of tactics. This refinement helps you to understand the full scope of an attack.
Mapping events to ATT&CK tactics is crucial for risk assessment. It enables you to identify high-risk areas and prioritize the development of new detections. This process leads to expanded security coverage.
For more information, visit MITRE ATT&CK.
Recommended steps of action: Actions that Contrast recommends to protect against the attack event.
Code location tab: Where available, details about the location in your code where Contrast detected the attack event. If no information is available, this tab is not displayed. The displayed details include:
File: The file associated with the attack event.
Method: The method associated with the attack event.
Stack: The code stack associated with the attack event.
Actions: These actions are available:
Configure a Protect rule to block or monitor the event
Add the source IP to the denylist
In the Add IP to denylist window, enter these details and select Add.
The name of the policy.
The IP address and, optionally, the subnet mask you want to deny. Classless Inter Domain Routing (CIDR) notation is supported for IPv4 and IPv6.
The IP source address for the selected event is displayed as the default value.
An expiration time.
Download the event details to a JSON file
Attack event views
Depending on whether you are using a grouped view or an individual view, the Attack Events list displays these details:
Column | Grouped view | Individual view |
|---|---|---|
Source IP | The IP address where multiple attack events originated. To see this detail for each attack event, select the group row or clear the Group by selection. | The IP address from which an attack event originated. |
Severity | A severity bar that shows the number of severity types for the attack events in the group. | The severity of the attack event:
|
Rules | The number of Contrast rules that the attack value violated. To see the name of the rule for each attack event, select the group row or clear the Group by selection. | The name of the Contrast rule that the attack value violated. |
Applications | The number of applications where Contrast detected the attack event. The see the names of the applications, select the group row or clear the Group by selection. | The name of the Contrast rule that the attack value violated. |
Servers | The number of servers where Contrast detected the attack event. To see the name of the server for each attack event, select the group row or clear the Group by selection. | The name of the server where Contrast detected the attack event. |
Detected | The time frame when Contrast detected the attack events in the group. To see the detected time for each attack event, select the group row or clear the Group by selection. | The time when Contrast detected the attack event. |
Result | A result bar that shows the number of result types for the attack events in the group. To see the result for each attack event, select the group row or clear the Group by selection. | The result for the attack event. The possible results are, in order of severity:
|
URL | Not shown. To view the URL for each attack event, select the group row or clear the Group by selection. | The path the attacker used for the attack event. |
Attack value | Not shown. To view the attack value for each attack event, select the group row or clear the Group by selection. | The value that the attacker sent that the Contrast agent detected was going to a sink. |
Actions | The possible action you can take for an attack event in the grouped view:
To view additional actions for each attack value, select the group row or clear the Group by selection. | The possible actions you can take for the attack event:
|