Deny or allow IP addresses
Use IP denylists or IP allowlists to manage IP addresses in your organization.
Before you begin
You can use Classless Inter Domain Routing (CIDR) notation to specify a subnet mask.
Steps
From the user menu, select Policy Management > IP Management.
Manage denylists:
Select the IP denylist tab.
To edit a denylist, select a denylist name, change the displayed information, and select Save.
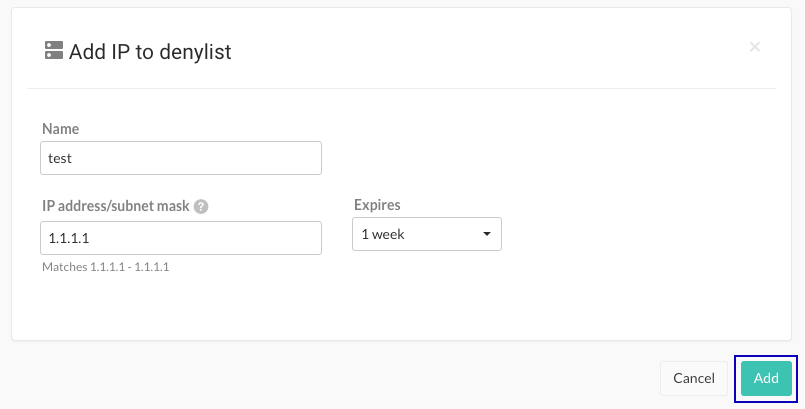
To add an IP address to a denylist, select Add IP to denylist, specify the details, and select Add.
Manage allowlists:
Select the IP allowlist tab.
To edit an allowlist, select the allowlist name, change the displayed information, and select Save.
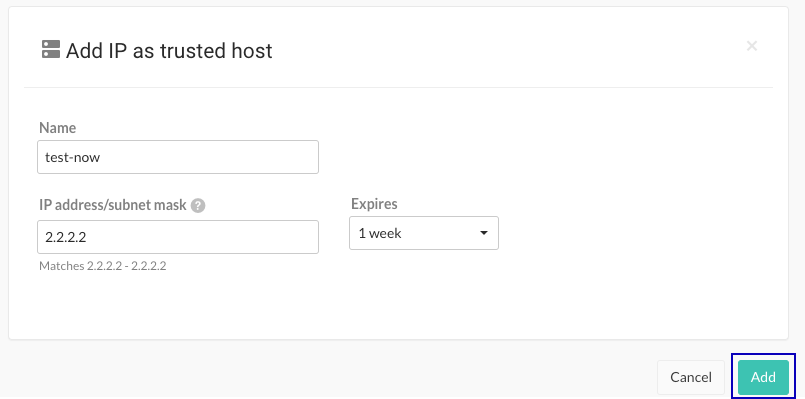
To add an trusted host to an allowlist, select Add trusted host, specify the details, and select Add: