Integrate with AWS Security Hub using Contrast Assess
Integrate Contrast Assess with AWS Security Hub to ensure a steady and secure transfer of security insights and findings directly to AWS, which helps in maintaining and enhancing your security posture through streamlined integration.
Before you begin
Before you start you must have:
AWS Account Number
AWS Region
The Contrast application from which to send insights
Configure
There are two required steps to configure this integration:
Configure AWS Security Hub to accept findings from Contrast
Configure Contrast Assess to send findings to AWS Security Hub
Configure AWS Security Hub to accept findings from Contrast
To allow AWS Security Hub to accept findings from Contrast:
Open the AWS Security Hub console associated with the AWS account and region where you want to receive findings from Contrast.
Go to the Integrations section and search for Contrast Security.
Locate the Contrast Security tile, click Accept findings and follow the subsequent prompts to complete the setup.
Continue with configuring Contrast Assess to send findings to AWS Security Hub.
Configure Contrast Assess to send findings to AWS Security Hub
After configuring the AWS Security Hub, the next step is to configure Contrast Assess to send the findings to the AWS Security Hub:
In Contrast, go to the user menu and select Organization settings > Integrations.
Find and select the AWS Security Hub integration section.
Select Manage Credentials.
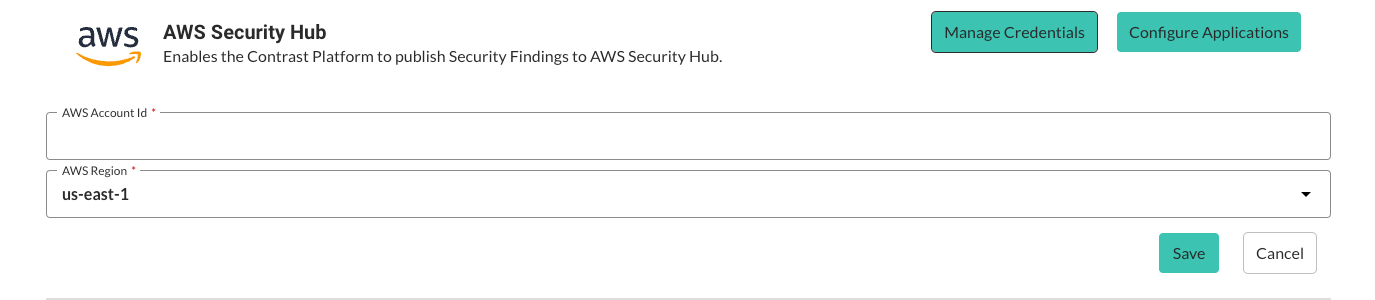
Enter the AWS Account number and select the AWS Region.
Select Save.
Continue by setting up applications in Contrast Assess.
Set up applications in Contrast Assess
Once your credentials are set up, proceed to configure the applications:
In the AWS Security Hub integration section in Contrast, select Configure Applications.
Select whether to activate the AWS Security Hub integration for all Assess applications or select specific application names from a list, choosing which insights to forward.
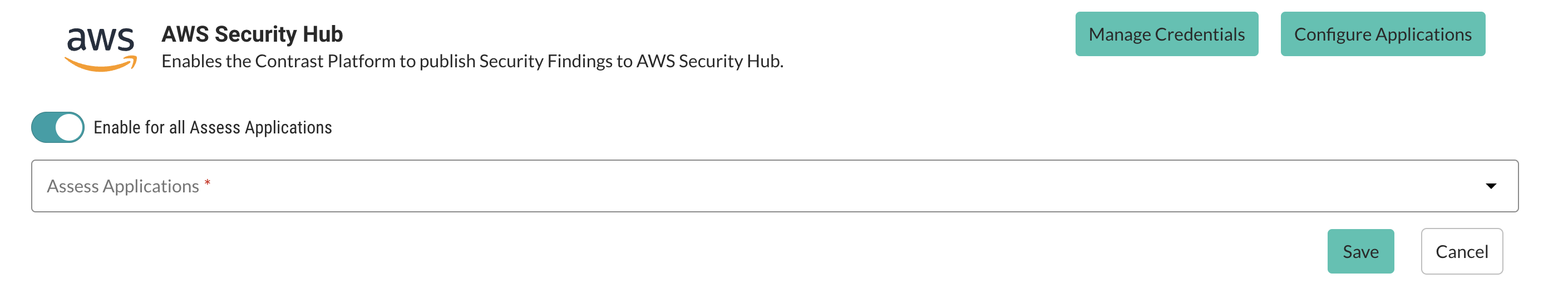
Select Save.
Retry mechanism
In case synchronization between Contrast Assess and AWS Security Hub fails, a retry mechanism ensures data reliability:
If an event fails to sync, it will be stored and retried every night at midnight GMT.
The retry count will increase by one with a maximum of three retries for up to 72 hours. After the third unsuccessful retry, the event will be discarded.
If a vulnerability creation event fails and is stored, any subsequent update or delete action relating to that failed event will be stored and replayed in chronological order to maintain the correct state.