Contrast Security Observability
Contrast Security Observability models an application’s security architecture and behavior at runtime.
Use this information to better understand the underlying behavior of your applications for threat modeling, pen test support, and contextual information around vulnerabilities and attacks.
Note
Currently, this feature is supported for Java, .NET Core, .NET Framework, Node.js, and Python applications.
Benefits
Once you add Contrast with security observability turned on for your applications, services, and APIs, you can quickly view in-depth details about their behavior and actions, such as:
Security defenses by resource, such as authentication (authn) and authorization (authz)
Potentially dangerous calls made during each of those resource calls (for example, SQL or system commands)
Backend connections for each resource
You can use this information for:
Threat modeling data flow diagrams
The observed data provides a ground-truth view into the behavior and architecture of your application that most impacts its security posture. You get:
Lightweight instrumentation of applications that offers continuous monitoring for high-performance examination of real application behavior.
Runtime visibility into application architecture, for example: Identification of all services, APIs, and files that the application accesses.
Penetration testing support
The observed data about your endpoints can help you effectively target your tests. You get::
Contextual behavior based on application utilization
Run time visibility in to application architecture
Vulnerability prioritization
The observed data provides information about a vulnerability's context to help you determine its impact and exploitability. You get:
Identification of services, APIs, files, and databases that the application accesses.
Attack context
The observed data provides context when a service or API is under attack. This data can help you determine its impact and exploitability.
Observe mode configuration
The observe mode setting in your agent's configuration file turns on the ability to view security observability details:
observe: enable: true
Once observe mode is turned on and you exercise your application, view the behavior insights from the Applications page in the Contrast web interface.
Runtime behavior insights
The runtime behavior insights that security observability provides includes these key details:
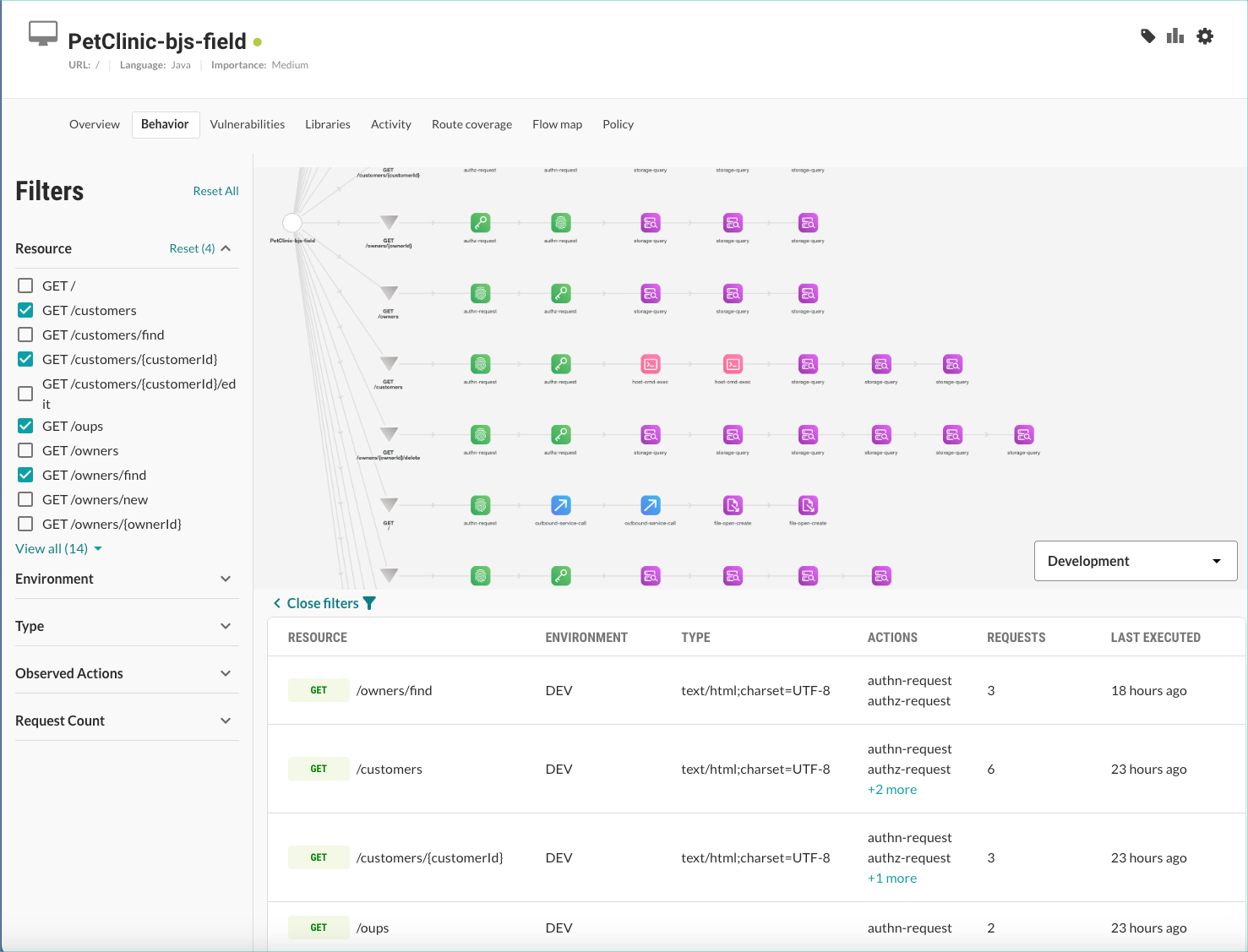
Application model: An graphical representation of the behavior and connections to other components that Contrast detects in an application.
Resource: Identifies an application’s entry points, such as routes used, message queues, web requests, and so forth.
Type: The response type that a resource uses. For example:
application/jsonortext/html.Actions: Security-relevant behavior that Contrast observes in the application, including:
Database connections, including the instance name of the database
File system access, including the name of the file or directory accessed
Outbound service or API calls
Authentication and authorization detection
System commands
Potentially dangerous functions
Security controls: Shows which of your service or API routes have custom security controls applied.
Environment: The environment where an action occurs: Development, QA, or Production.
Requests: The number of requests made for the resource.
Last executed: The last time a resource was exercised in the application.