View issues with Northstar
Issues represent a security problem that you can fix in a single place. The information is most useful for AppSec teams and developers.
An issue comprises all the observations from the Contrast AST and ADR technologies that Contrast correlates together.
Use the filters to refine the view. Refining the view lets you filter, triage, and prioritize the Issues list based on what Contrast analyzed and how the issue is detected.
How Contrast creates issues
Contrast automatically creates issues when an application instrumented with a Contrast agent is attacked. When Contrast detects a new vulnerability, it generates an issue. Any attack event that has a status of exploited, suspicious, or blocked also results in the creation of issues.
Before you begin
Actions and permissions lists the permissions you need.
Steps
To view a list of issues, from the left navigation, select Issues.
To sort the view according to ascending or descending order, select the arrow (
icon next to a column heading.
The list displays these details for each issue:
Severity: The severity that Contrast assigns to the issue.
Contrast score: The Contrast score represents the risk of an issue or incident at a particular point in time. Contrast determines this score by using information from the Contrast SAST, IAST, SCA, ADR, and Observability technologies.
Contrast uses the Common Vulnerability Scoring System Version 4 (CVSS 4) standard as the primary framework for calculating the score.
Issue: The issue type and location. For example, SQL Injection from "userid_6a" Parameter on "/WebGoat/SqlInjectionAdvanced/attack6a" page
Issue ID: An identifier that Contrast assigns to the issue. It has this format:
ISS-<year>-<numberOfIssues>For example,
ISS-2025-10represents an issue that occurred in the year 2025 and was the 10th issue that Contrast reported.Status: The status of the issue: Open or Closed.
Application: The name of the applications where Contrast observed the issue.
To view the relationships between the application and its associated entities (servers, called APIs, and databases), select the application link to open the view in Explorer.
Number of observations: The number of times that Contrast observed this issue.
Last detected: The last time that Contrast detected the issue in the application.
Most recent incident: The date of the most recent incident associated with the issue.
To view details about a specific issue, select it. The Overview tab shows these details:
Issue ID: The identifier that Contrast assigned to the issue.
Associated application: The application where Contrast observed the issue.
Severity: The severity level that Contrast assigned to the issue.
Status: The status of the issue: Open or Closed.
First detected: The date when Contrast first saw the issue.
Last detected: The date when Contrast last saw the issue.
Rule: The Contrast rule associate with the issue.
MITRE: A link to the MITRE ATT&CK tactic associated with the issue.
The MITRE ATT&CK framework is a knowledge base of adversary tactics and techniques derived from real-world observations.
A single attack event can map to multiple tactics. In the case where multi-stage attacks events occur, an observed event might represent a single action within a larger attack chain. Alternatively, it could indicate a threat vector.
Combining event data with context from other security tools, such as Web Application Firewalls (WAFs) or Endpoint Detection and Response (EDR) solutions, allows for more precise identification of tactics. This refinement helps you to understand the full scope of an attack.
Mapping events to ATT&CK tactics is crucial for risk assessment. It enables you to identify high-risk areas and prioritize the development of new detections. This process leads to expanded security coverage.
For more information, visit MITRE ATT&CK.
Data type: The source of the issue.
Target: What Contrast analyzed: code or a library.
Sensor: How Contrast detected the issue. The current value is Contrast agent.
Technique: The analysis technique: static or runtime.
Associated assets: The servers and environments associated with the issue.
Associated incidents: The incidents that Contrast created for the issue.
How to fix: Guidance for fixing the issue, including details from Contrast Intelligent Remediation and if available, Contrast runbooks.
To view the activity log for incidents, select the Activity tab.
To view all the activity from Contrast and activities related to issue changes, select the All tab.
Use the Recent filter to change the order from most recent to oldest.
To view comments, select the Comments tab
To add a comment, enter the comment in the Add comments box and select the arrow icon.
To view the data that led Contrast to create an issue, select the Evidence tab. Depending on the issue type, this tab could include information such as:
HTTP info Details for the HTTP request.
This section is available only when the vulnerability has HTTP information associated with it
Details such as (displayed categories vary depending on the issue type):
HTTP parameter found in the request
Data flow from the parameter to the return value
String operations that occurred (includes the line number of the code)
Rule violations
Untrusted data
And more...
For additional details, expand any of the Details categories to view:
Class methods
Objects
Return values
Parameters
Stack traces
Use the filter to view stack traces for all code, library code, or custom code.
To view a list of Contrast observations, select the Observations tab. The list of observations includes these details:
Source IP: The IP address where an event originated.
Rule: The name of the Contrast rule that the observed value violated.
Application: The name of the application where Contrast detected an attack event.
To view the relationships between the application and its associated entities (servers, called APIs, and databases), select the application link to open the view in Explorer.
Server: The name of the server where Contrast detected the attack event.
Detected: The time when Contrast detected the attack event.
Result: The result for the attack event. The possible results are, in order of severity:
Exploited:
Contrast detected an attack event at the perimeter and confirmed it at the sink. The mode is set to Monitor.
Maps to this severity: Critical or High
Suspicious:
Contrast detected a low confidence attack event at the perimeter for a perimeter-only rule in Block mode.
Contrast detected a high or low confidence attack event at the perimeter for a perimeter-only rule in Monitor mode.
Contrast detected an attack event using sink-only heuristics. The mode is set to Monitor.
Maps to this severity: Medium
Blocked:
Contrast detected an attack event at the perimeter and confirmed it at the sink. The mode is set to Block.
Contrast detected an attack using sink-only heuristics. The mode is set to Block.
Maps to this severity: Informational
Probed:
Contrast detected an attack event at the perimeter, but did NOT confirm it at the sink. The mode is set to Block or Monitor.
These are ineffective attacks that can indicate an attacker is probing, scanning, or fuzzing your application for vulnerabilities.
Maps to this severity: Low
URL: The path the attacker used for the attack event.
Value: The value that the Contrast agent detected was going to a sink.
Refine the view
To refine the view (including the details view), open the filter panel by selecting the Filter icon () at the top right of the list and selecting one or more filters.
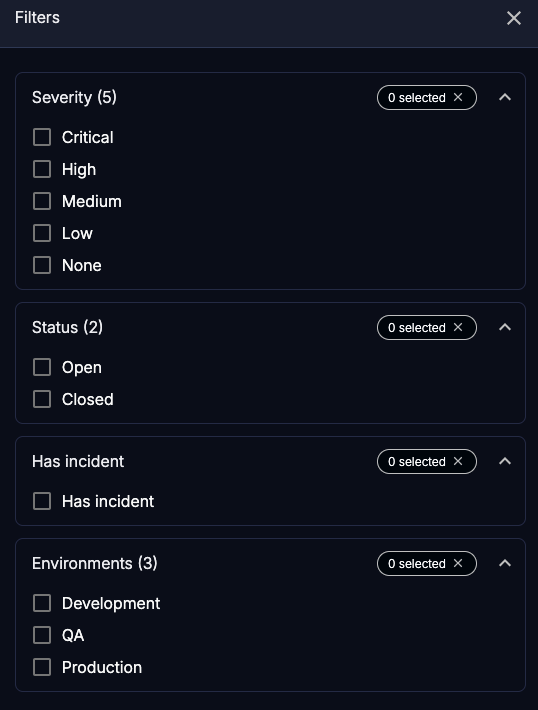
The available filters are:
Time: The time frame for the view
Select a displayed time frame or select Custom to specify a customized time frame.
Severity: The severity of the incident: Critical, High, Medium, Low, Note, None
Status: The status of the incident: Open or Closed
Root Library name: The name of a root library.
Use the Search box to find specific libraries.
Has incident: The issues that have associated incidents
Environments: The environments where Contrast found the issue: Development, QA, and Production
Data type: The source of the issue. Current filters are Vulnerability (from Assess) and Attack (from ADR or Protect).
Target: What Contrast analyzed. The current filters are Code and Library.
Sensor: How Contrast detected the issue. The current filter is Contrast agent.
Technique: The analysis technique. The current filters are Runtime and Static.