Integrate Splunk with Contrast
The Contrast Security App for Splunk provides actionable and timely application threat intelligence across your entire application portfolio. Contrast Security instrumented applications self-report these details about an attack:
The attacker’s IP address
Authenticated username
Method of attack
Affected applications and servers
Attack frequency and volume
Level of compromise
Before you begin
Ensure you have the following software:
Splunk Enterprise or Splunk CloudPlatform, versions: 9.3, 9.2, 9.1, 9.0, 8.2, 8.1, 8.0
Contrast Security App for Splunk 2.0.1 or later
Applications instrumented with a Contrast agent
Step1: Install Contrast Security App
For more guidance installing Splunk applications, visit their documentation.
Install the app
In Splunk, select Apps.
Search for Contrast Security App for Splunk.
Select Install.
After installation, you should see the Contrast Security App in the Apps dropdown.
Install the app from a file
Log in to Splunkbase.
Search for the Contrast Security App.
Select download and save the file to a convenient location.
In Splunk, select Apps.
Select Manage.
Select Install app from file.
Select the app you downloaded.
Optionally, select Upgrade app if you installed the Contrast Security app previously.
Select Upload.
Step 2: Set up a syslog receiver in Splunk
Contrast agents stream SIEM events as UDP syslog events in CEF format.
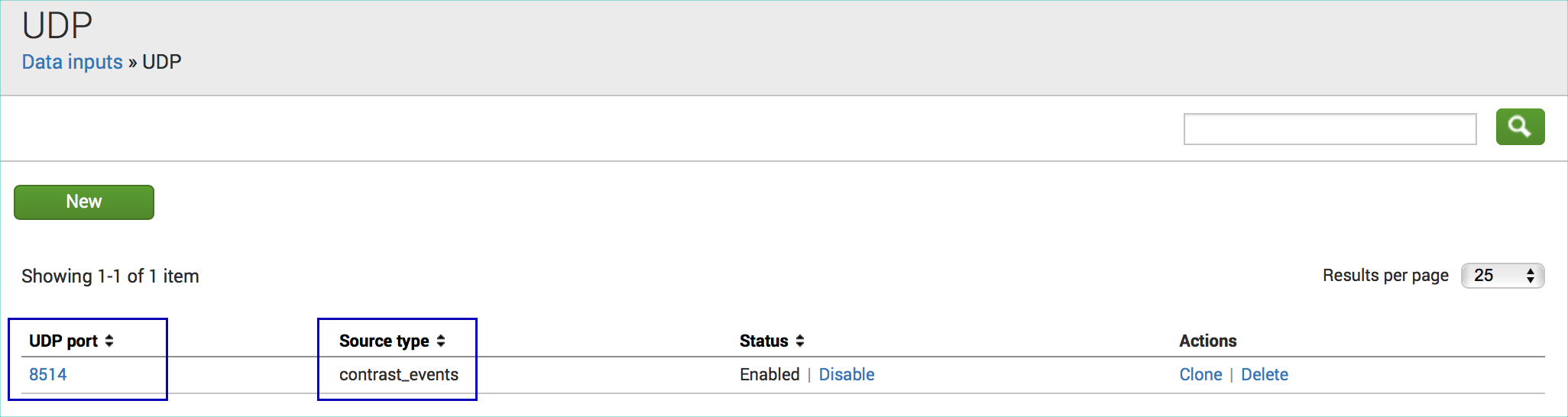
In Splunk, select Settings > Data Input.
Add a new UDP listener.
Reuse port 514 or chose a different port.
For the source type, specify
contrast_events.Select Save.
Step 3: Set up Contrast agents
Setup for a single server in the Contrast web interface
In the header, select Servers.
Select a server that has Protect turned on.
Select the Settings icon (
) in the top right of the page.
In Server settings, select Enable output of Protect events to syslog.
Specify the settings for the syslog output:
Fully Qualified Domain name for the Splunk server where you want to send messages,
The UDP port
Syslog facility (the process that created the message)
The syslog message severity levels
Select Save.
Setup for all new servers in the Contrast web interface
From the user menu, select Organization settings.
Select Servers.
Select Enable output of Protect events to syslog.
Specify the settings for the syslog output:
Fully Qualified Domain name for the Splunk server where you want to send messages,
The UDP port
Syslog facility (the process that created the message)
The syslog message severity levels
Select Save.
Setup with agent configuration files
Specify the syslog settings in the agent configuration YAML file, as shown in this example:
agent: syslog: enable: true ip: splunk.mycompany.org port: 8514 facility: 12 # Set the log level of Exploited attacks. Value options are `ALERT`, # `CRITICAL`, `ERROR`, `WARNING`, `NOTICE`, `INFO`, and `DEBUG`. severity_exploited: CRITICAL # Set the log level of Blocked attacks. Value options are `ALERT`, # `CRITICAL`, `ERROR`, `WARNING`, `NOTICE`, `INFO`, and `DEBUG`. severity_blocked: WARNING # Set the log level of Probed attacks. Value options are `ALERT`, # `CRITICAL`, `ERROR`, `WARNING`, `NOTICE`, `INFO`, and `DEBUG`. severity_probed: NOTICE
Step 4: View Contrast data in Splunk
Splunk provides three dashboards where you can see Contrast data.
In Splunk, under Apps, find Contrast Security for Splunk.
Select Dashboards.
Select a dashboard:
Attack Dashboard: This dashboard shows a summary of attacks that Contrast blocked in a specified time frame, identifies which applications are targeted for attacks, the type of attacks and when they occurred., and the most frequently targeted URIs.
Attacks by Applications: For the specified applications, this dashboard shows the number of attacks , the different types of attacks detected and blocked, the distribution of different attack types in a specified time frame, and the top 10 most attacked URIs.
Attacks Geographical Distribution: This dashboard shows a geographical view of attacks that Contrast Security detected and blocked.
See also
These topics provide details for agent-specific syslog settings in agent configuration files: