Security controls
A security control is a method in your code that ensures the data passing through it is safe to use in your application. Contrast trusts information that is passed through built-in security controls it knows about. Contrast monitors many methods from third-party libraries to determine whether a data flow is safe.
In some cases, your organization may choose to build its own security controls which are not known to Contrast. For these cases, create security controls that teach Contrast to account for your custom method. Adding custom security controls results in Contrast reporting more accurate results.
Types of security controls
Input validators: Validators are methods that ensure only properly formed and formatted data is accepted as input before it’s passed to other parts of the application. They are designed to allow the input field to accept or reject specific characters.
Input validation is the primary method of preventing SQLi, XSS, and other input-validation related attacks.
Regex validators: Regex validators compare a specified regex pattern in an input string to validate whether it's safe. If a string matches the regular expression specified in a security control, Contrast suppresses related vulnerabilities. Regex validators are applied on an application-specific basis.
Sanitizers: Instead of validating input, sanitizers render input safe before it’s passed to other parts of the application, like databases. For example, a sanitizer might take a single quote that could be used in a potential injection attack and change it to double quotes.
When to use security controls
Create security controls when Contrast does not have visibility into methods, classes, or libraries that your application is using to protect it from input validation issues (sanitizers, input validators, and regex validators).
If you know about the validators or sanitizers that your applications use, you can add them manually or move a suggested security control that Contrast detects automatically to the list of security controls that you apply to your applications.
After you add and enable security controls, they suppress input vulnerabilities in Assess that the security control is designed to mitigate. It is very important that you apply your security control to the proper vulnerability rule.
Effects of using security controls
Security controls affect any vulnerability and detection for specified rules. Input validators and sanitizers are usually designed for or are applicable to a specific type of data, a particular field, page, or specific application. Enabling a security control for all rules can result in false negatives findings.
Use security controls carefully. You might need to apply a security control to specific rules only. For example, if a validator or sanitizer protects your application from XSS, it may not be effective against SQL injection. If you apply a security control to all rules, Contrast would likely suppress aSQLi vulnerability which would results in false negative finding.
A security control should be good enough to assure you that is it protecting your application against a wide range of attacks.
Roles for security controls management
Only users assigned an organizational role of RulesAdmin or higher can view or modify security controls.
Supported languages
Security controls for input validators and sanitizers apply to Java, .NET Framework, and .NET Core languages only.
Security controls for regex validators apply to the Java language only.
Security control example
Assume that you have a method called DoLegacySecurity() inside a class called com.Acme.OldSecurity that is being reported for using insecure cryptographic algorithms, You create a security control and specify this method signature:
com.Acme.OldSecurity.DoLegacySecurity(java.lang.String*)
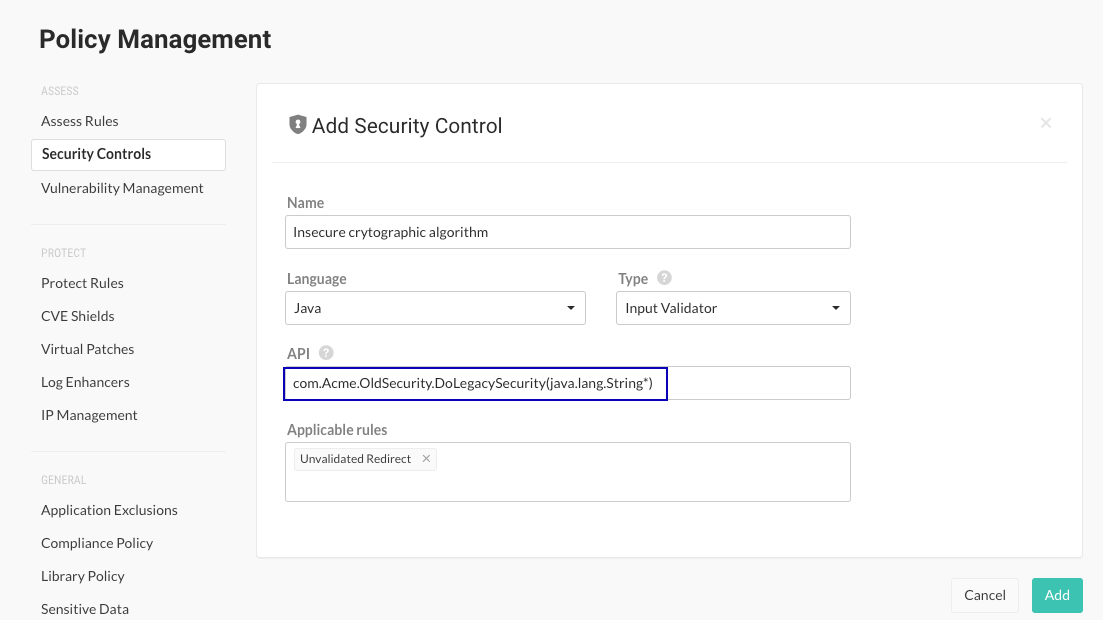
In this example, Java.lang.String* is the marked parameter to be validated.
When creating the security control, you are careful to not include any trailing parameter definitions or extra characters.
Contrast matches this method signature against the stack trace for any vulnerabilities it finds and suppresses them.