SARIF file data
When you download results, Scan writes the data to a SARIF file.
SARIF is a standard data model and serialization format for static analysis results. Understanding the data in the SARIF file can help when you need a deeper understanding of scan results.
The SARIF file includes this type of information:
Information about the scanner that Contrast uses
Data on what was scanned and the scan composition
Data on vulnerability findings
Errors or notifications that are handled gracefully during the scan
Scan coverage data
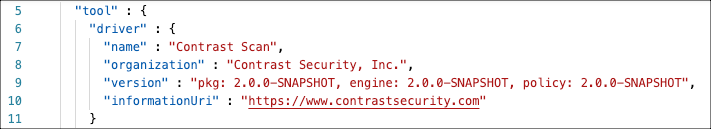
Scanner data
This example shows data about the scanner that Contrast uses:
Vulnerability data
The examples in this section show some of the data for a single vulnerability. The scan shows this data in the results section.
Single object
This example shows the scan results for a SQL injection vulnerability. The data in the
threadFlowssection show the scanned data from the source to the data sink.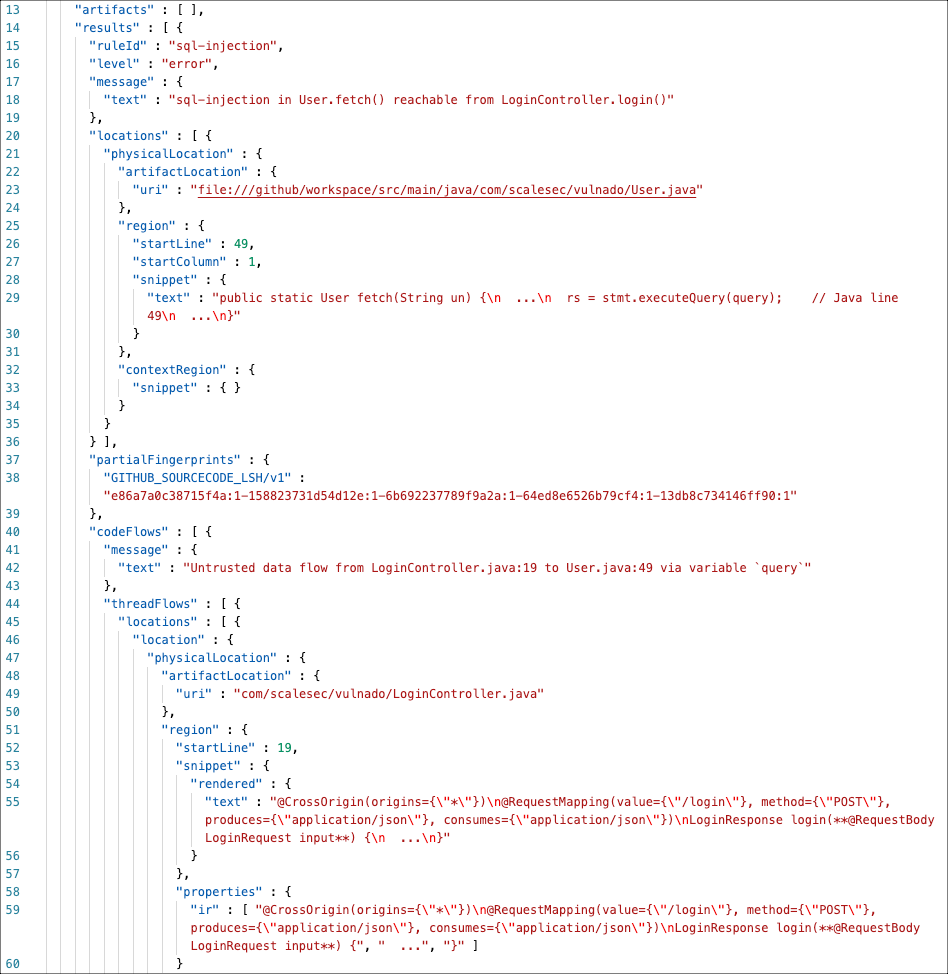
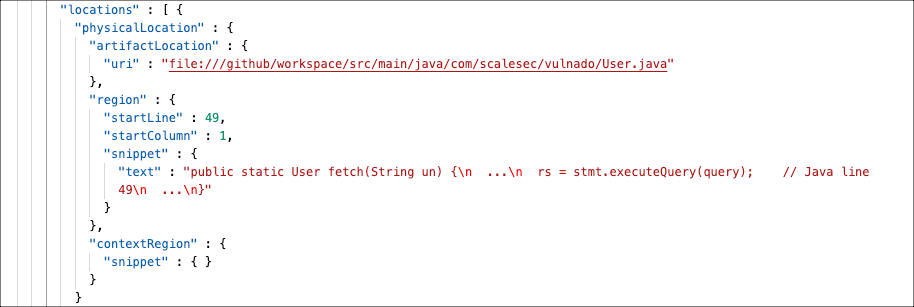
Sink location
This example shows the sink or problem location for the vulnerability.
Thread flow steps
This example shows some of the data for one execution step in the data flow:
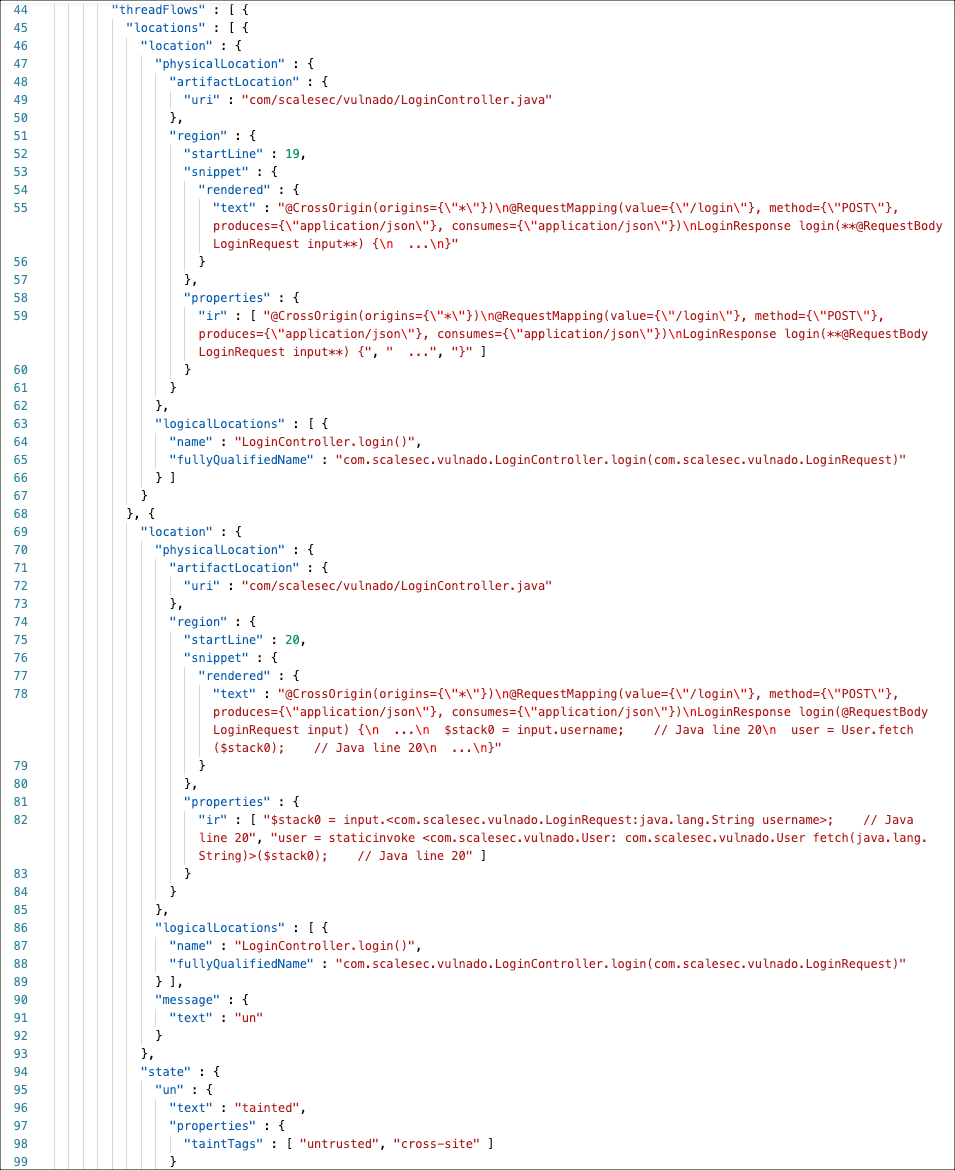
Physical and logical locations of the vulnerability
This examples shows data for physical and logical locations of a vulnerability:
The data for execution steps in this section includes a code snippet and rendered data from intermediate representation (IR) data (user code is not usually displayed). Contrast uses this data to analyze what the scan sees.
This example shows the execution statement from IR.
This example shows the general area where an execution step occurs in the application.
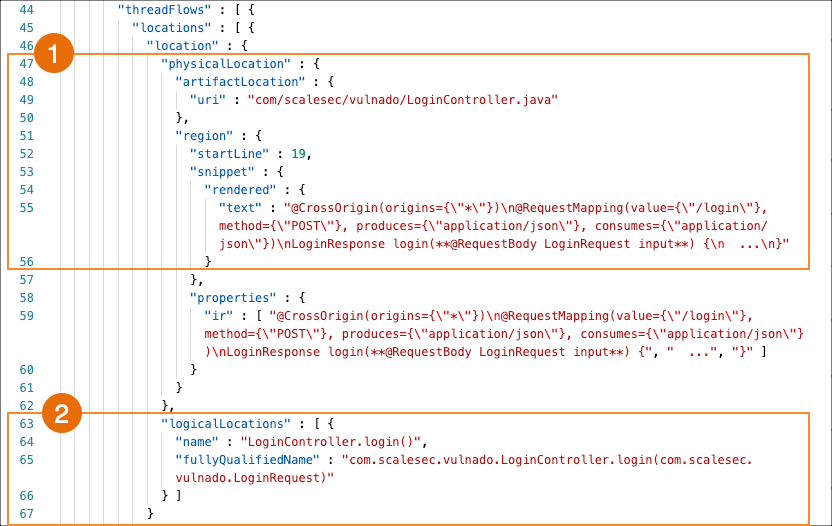
Untrusted data location
These examples shows scan results for untrusted data.
Scan looks at executions steps from code source to data sink. The scan results include any execution step that touches untrusted data.
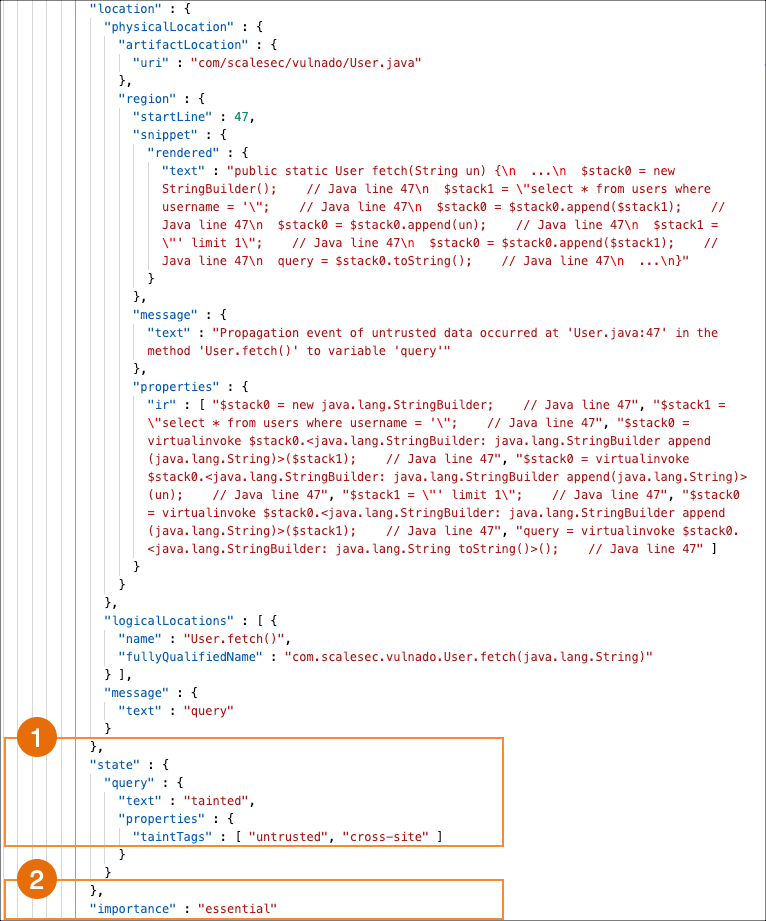
If the
importanceresult isessential, check this area of the code for vulnerabilities.This example shows the location of tainted data that the scan is tracking.
This example shows the location of the tracked data that the execution step touches. The scan results indicate the
importanceisessential. This code needs to be checked for vulnerabilities.
Scan analysis
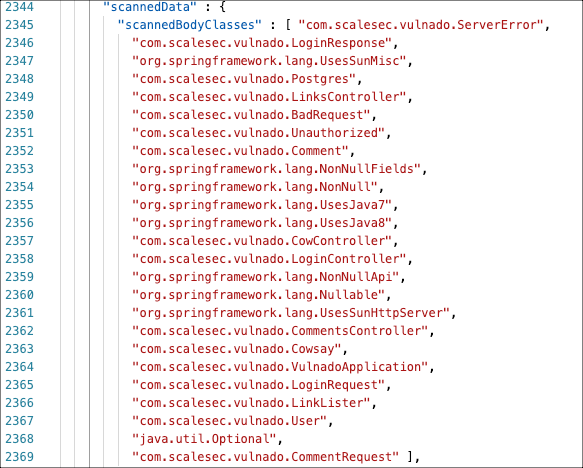
The examples in this section show how to identify content in the SARIF file that can help you analyze scan results.
Classes that scan uses to trace data
These classes affect scan execution time.
Classes used for type hierarchy resolution
Scan uses these classes only for type hierarchy resolution.
The library classes are either not relevant to security issues or Contrast has a specific policy for the relevant API.
If a class displayed in this section is related to custom code, it is possible that the scan results contain false negatives.
Phantom classes
Phantom classes are referenced classes but either Scan is unable to find bytecode for them or Scan was unable to decompile the code into IR.
Ideally, the scan results should contain no phantom classes. If the results include phantom classes, Scan was unable to find the data it needed to provide more accurate results. If you see application code or libraries displayed in this section, look at your code to determine if an issue exists.
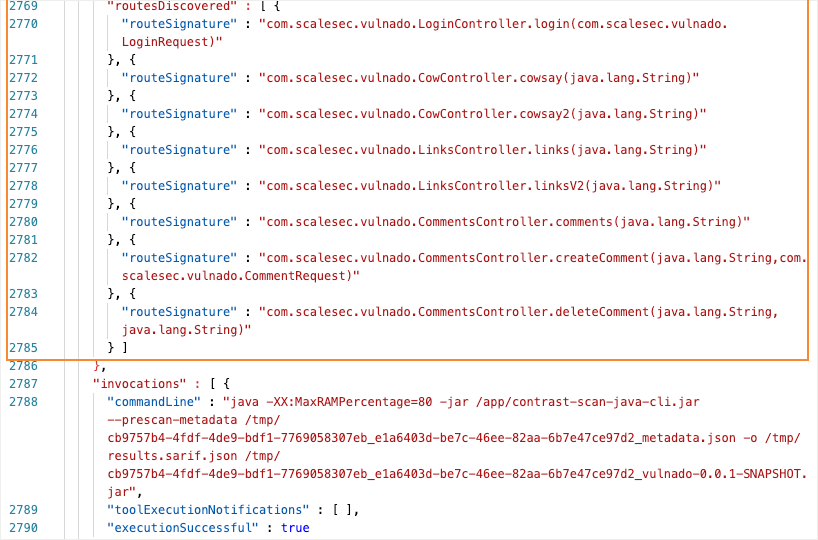
Discovered routes for untrusted data
This example shows discovered routes where untrusted data enter the application.
Scan only looks at the data flow behavior from the functions displayed in this section. Scan does not analyze other functions related to data flow, such as weak cryptography.