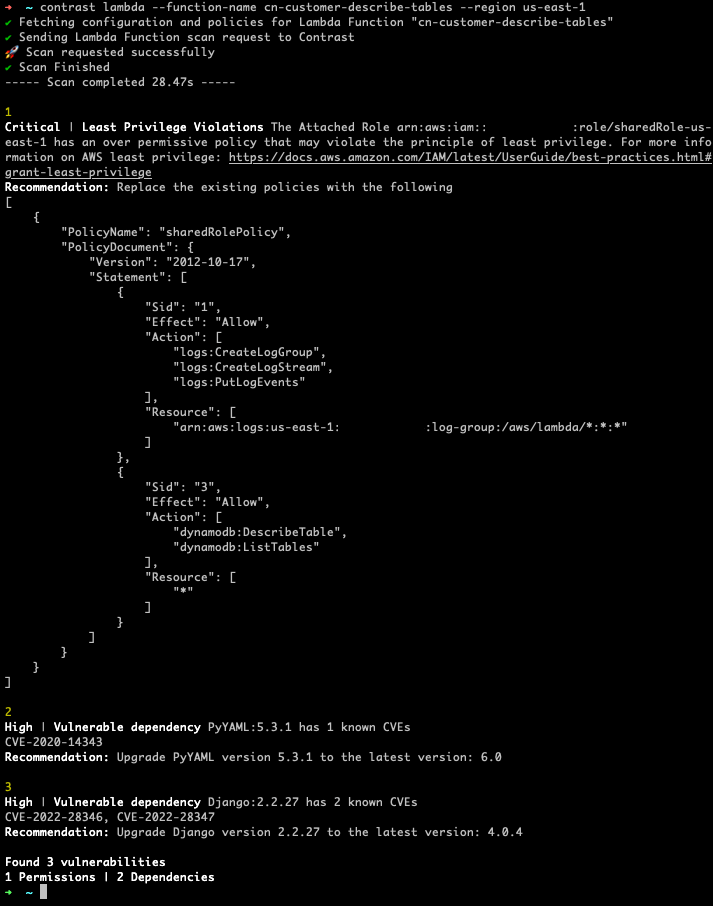
Run a scan on a Lambda function with Contrast CodeSec
CodeSec by Contrast Security helps you find and fix security issues on AWS lambda functions. It currently supports Java and Python functions on AWS.
By running a scan on your lambda functions, you can find:
Least privilege identity and access management (IAM) vulnerabilities (over permissive policies) and remediation
The Common Vulnerabilities and Exposures (CVE) from your libraries (Vulnerable Dependencies) and remediation
Before you begin
Configure AWS credentials on your local environment by running the commands with your credentials:
export AWS_DEFAULT_REGION=<YOUR AWS REGION>
export AWS_ACCESS_KEY_ID=<YOUR ACCESS KEY ID>
export AWS_SECRET_ACCESS_KEY=<YOUR SECRET ACCESS KEY>
AWS credentials should be available on your local configure (usually ~/.aws/credentials). You have an option to run a lambda scan with your aws-profile to pass --profile. You also can export different credentials.
These permissions are required to gather all required information on an AWS Lambda to use the contrast lambda command:
Lambda: GetFunction | GetLayerVersion | ListFunctions
IAM: GetRolePolicy | GetPolicy | GetPolicyVersion | ListRolePolicies | ListAttachedRolePolicies
Step 1: Run a scan
Use Contrast lambda to scan your AWS Lambda functions.
contrast lambda --function-name MyFunctionName --region my-aws-region
Step 2: View results