Configure single sign-on (SSO) at an organization level
For on-premises customers, single sign-on can be configured at a system level. For hosted customers, Contrast Security configures authentication; however, a user may be granted permissions to set up SSO for their organization.
Note
If users are identified with a user ID rather than an email address, those accounts don’t automatically transfer over to the SSO configuration and must be recreated.
If you configure SSO in Contrast and also want to use multi-factor authentication, configure it by using your identity provider (IdP), instead of Contrast. With SSO configured, Contrast passes the responsibility of authenticating users to the IdP.
After configuring SSO for the first time in a hosted installation, it can take several minutes for the configuration to take effect.
If you're not using SSO, protect your system by requiring multi-factor authentication as a required setting.
From the user menu, under Organization settings, select Single-sign-on and select Get started.
To change an existing configuration, select Edit at the bottom of the screen.
In the left navigation, under Administration, select Single-sign-on.
You may receive a warning window regarding the implications of changing authentication. Read it carefully before proceeding.
Use the displayed information at the top of the screen to set up Contrast with your IdP.
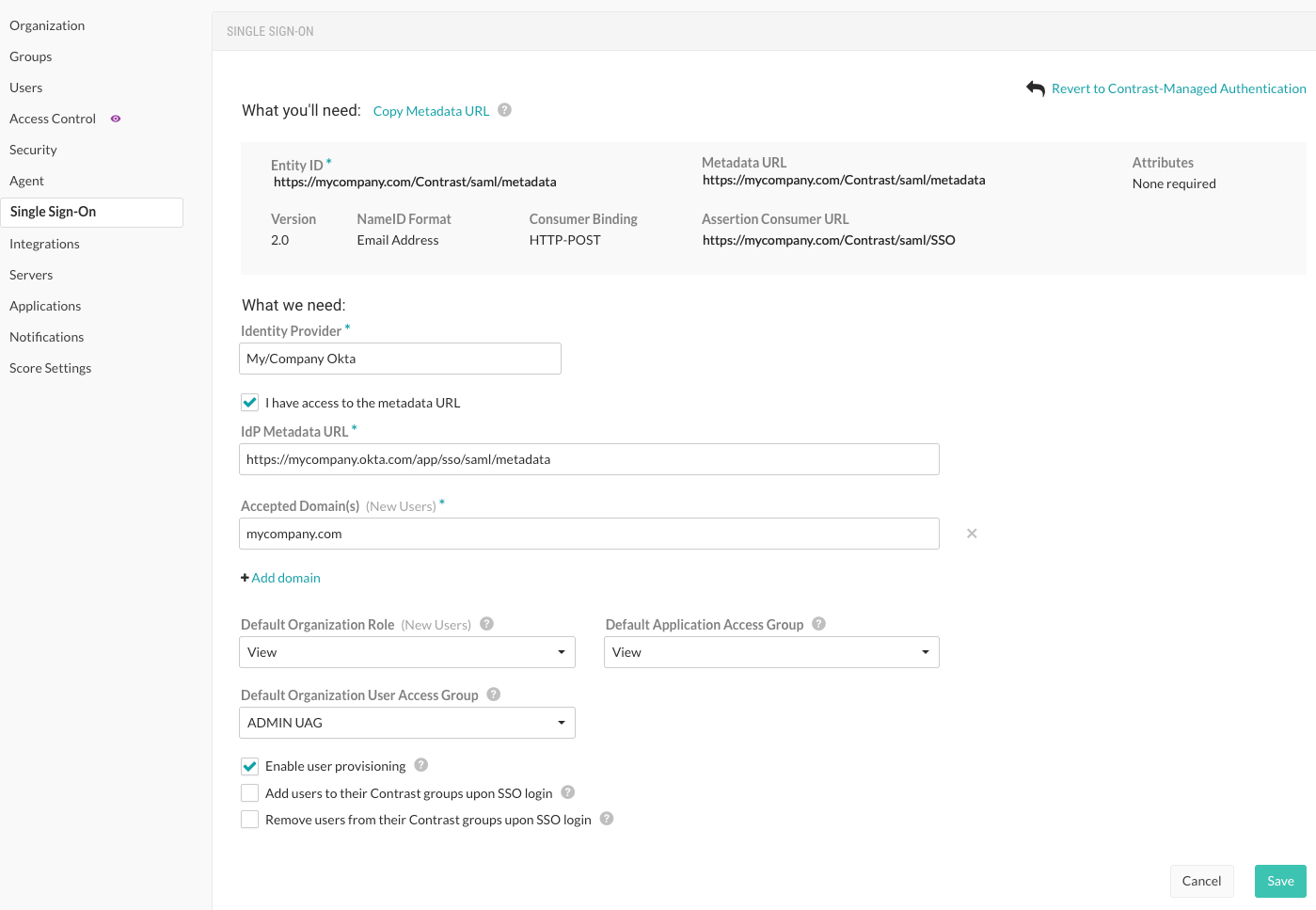
Provide a name for your IdP as well as the associated metadata to connect to Contrast.
If you want to automatically create new user accounts when someone make a SAML request to log in to Contrast, select the Enable user provisioning checkbox at the bottom of the screen.
Add the Accepted domains that must be used to trigger user provisioning (for example,
contrastsecurity.com)Specify roles and groups:
On-premises customers: Use the dropdowns to choose the Default organization role and Default application access group for the new users.
The value displayed for the Default User Access group does not apply to your configuration.
Hosted customers: If role-based access control is turned on, use the dropdown to select a Default User access group for the new users.
The values displayed in the Default organization role and Default application access group do not apply to your configuration. If you are using the legacy access control, follow the instructions for on-premises customers.
If you want to add users who are members of a SAML group that matches the name of a Contrast group, select Add users to their Contrast groups upon SSO login.
If you want to remove users who are members of a SAML group that does not match the name of a Contrast group, select Remove users from their Contrast groups upon SSO login .
Select Save.
Open a new browser window, private browsing session or incognito window, and attempt the SSO login with your account. If you're unsuccessful, go back to the browser in which you're still logged in, disable SSO for the organization, select Revert to Contrast-managed authentication and confirm the change.
