Integrate with Amazon Security Lake using Contrast Assess
Integrate Contrast Assess with Amazon Security Lake to push findings and other relevant security data automatically.
Before you begin
Before you start, you must have:
AWS Region
Create a Custom Source in AWS
In AWS, go to Amazon Security Lake.
Select Custom Source.
Click Create New Source.
Enter a Data source name of your choice.
Set the OCSF Event class to Security Finding.
Input the AWS account ID and External ID.
These IDs are under the Amazon Security Lake section on Contrast's Integrations page. From the user menu in Contrast select Organization settings > Integrations.
Once a custom source is created, retrieve the generated Role ARN and the S3 ARN. You will need these to connect to AWS.
Continue with connecting to Amazon Security Lake.
Connect to Amazon Security Lake
In Contrast, go to the user menu and select Organization settings > Integrations.
Find and select the Amazon Security Lake integration section.
Select Manage Credentials.
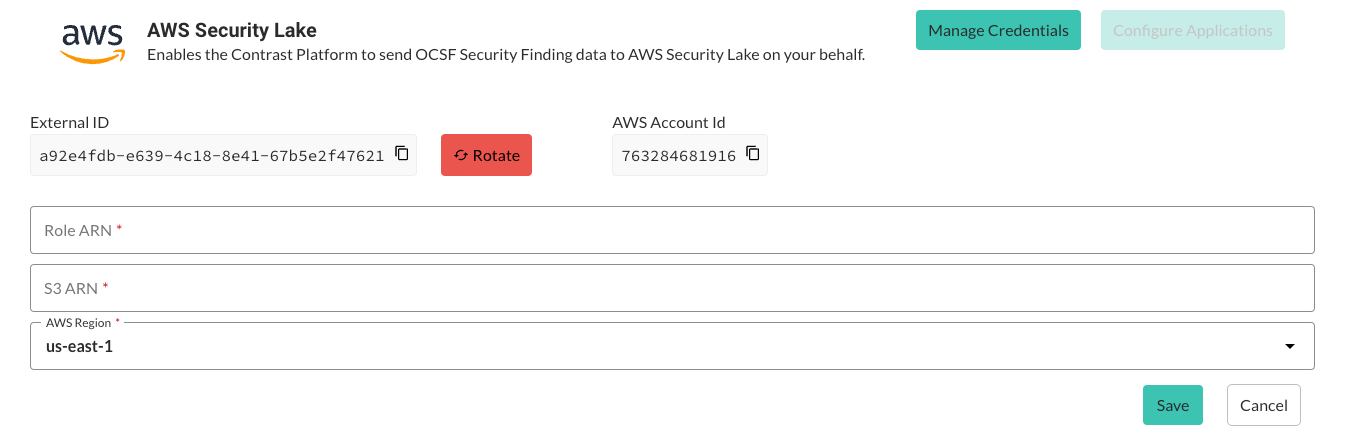
Enter the generated Role ARN and the S3 ARN from before.
Choose the AWS Region from the list or enter it manually.
Select Save.
Continue by setting up applications in Contrast Assess.
Set up applications in Contrast Assess
Once your credentials are set up, proceed to configure the applications:
In the Amazon Security Lake integration section in Contrast, select Applications.
Select whether to activate the Amazon Security Lake integration for all Assess applications or select specific application names from a list.
Select Save.
Retry mechanism
In case synchronization between Contrast Assess and Amazon Security Lake fails, a retry mechanism ensures data reliability:
If an event fails to sync, it will be stored and retried every night at midnight GMT.
The retry count will increase by one with a maximum of three retries for up to 72 hours. After the third unsuccessful retry, the event will be discarded.
Suppose a vulnerability creation event fails and is stored. Any subsequent update or delete action relating to that failed event will be stored and replayed in chronological order to maintain the correct state.