View audit log 
Contrast captures activity about user sessions including changes to settings or licenses, actions on vulnerabilities, and much more.
This view is for on-premises customers. If you are a hosted customer, visit View audit log (hosted customers).
Steps
Under the User Menu, select Organization Settings > Security.
Select View Audit Log on the upper-right of the page.
Use the search fields to look for a specific log by date or name.
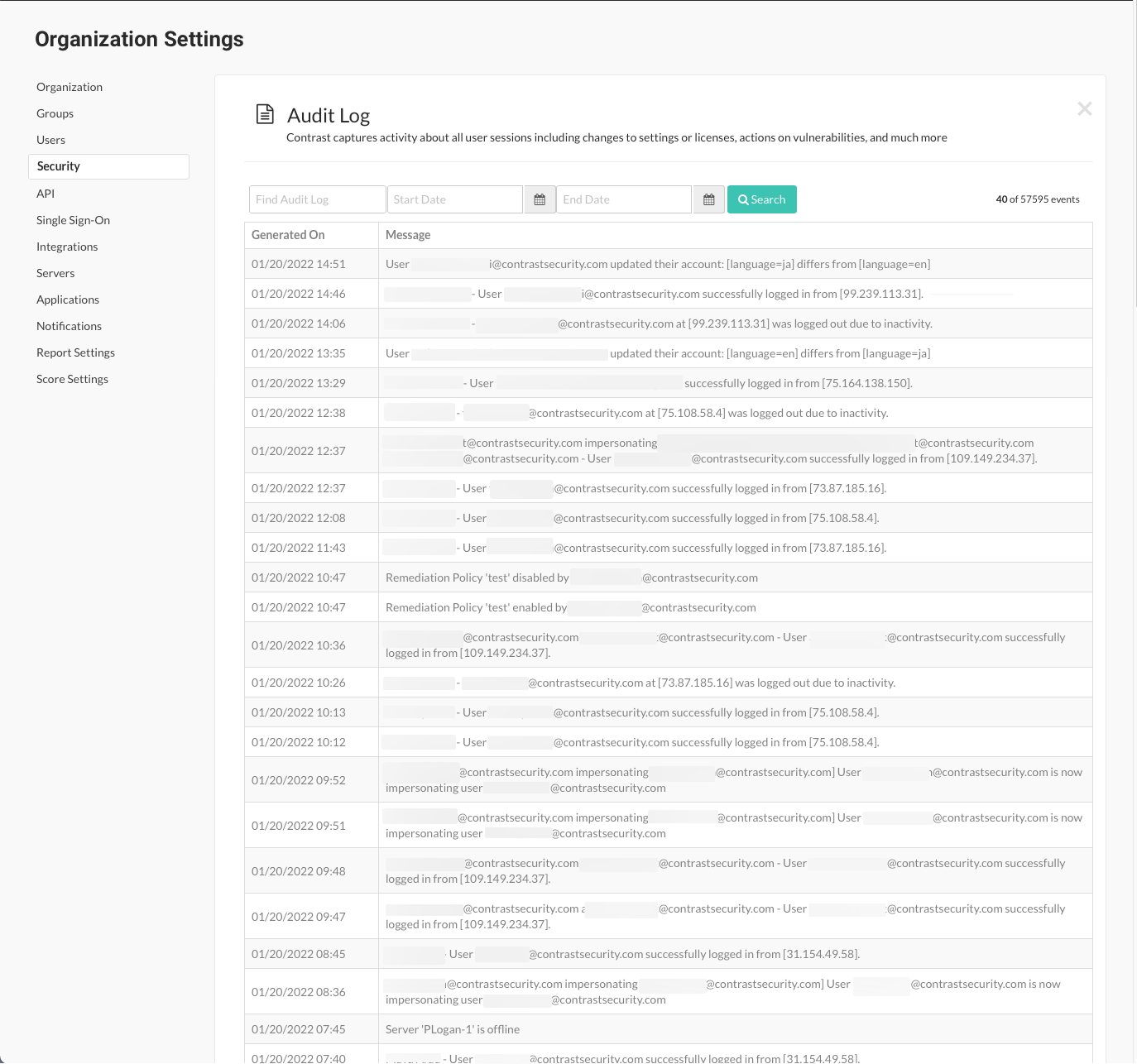
Audit log details
The audit log contains these details:
Alerts | Creating Deleting Updating |
Applications | Applying a license Archiving Changing Assess rule configurations Changing organization settings Changing application metadata settings Enabling/disabling a rule Merging/unmerging Restoring Resetting |
Attacks | Adding notes to events Creating/Editing/Deleting notes Suppressing |
Bugtrackers | Creating Updating |
Adding domains Sharing libraries | |
Groups | Creating/Updating/Modifying membership of organization groups |
IP ranges | Adding Removing |
Keys | Rotating API and Agent service keys |
Notification settings | Updating for an organization or user |
Patches | Creating/Updating/Toggling/Deleting virtual patches |
Policies | Changing cleanup settings Changing library restrictions Changing password Changing scoring Changing timeouts Creating/Deleting/Disabling/Enabling/Updating compliance policies Creating/Deleting/Updating/Enabling organization remediation policies Creating/Deleting/Updating/Enabling security controls Creating/Deleting/Updating/Enabling rule exclusion policies |
Reports | Creating reports Vulnerability trend reports |
Role-based access control Role-based access control is a preview feature and not turned on for all users. | Creating/Updating/Deleting users Creating/Updating/Deleting resource groups Creating/Updating/Deleting roles: Includes updates to built-in roles. Creating/Updating/Deleting user access groups |
Scan | Creating/Deleting scan projects Running a scan Changing the status of a vulnerability |
Servers | Changing defaults Creating notifications Deleting/Disabling/Updating/Removing licenses Enabling/Disabling Protect |
SuperAdmin | Creating Impersonating a user Updating |
Traces | Adding/Editing/Deleting notes Auto-remediation Sharing/Deleting/Merging/Marking status of a trace (or bulk traces) Updating severities |
Users | Adding Activating Changing access Creating/creation via provisioning/in bulk Deleting Granting/Revoking Protect Importing into an organization Underprivileged user attempts Updating |
Webhooks | Creating |