AWS policy and permissions for running Contrast Serverless
This is a sample of how to obtain the policy and permissions for your AWS account with Contrast Serverless.
Obtain a policy
This is a sample updated policy for an account.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "CustomResources",
"Effect": "Allow",
"Action": [
"sns:Publish"
],
"Resource": "*"
},
{
"Sid": "SNS2",
"Effect": "Allow",
"Action": [
"sns:CreateTopic",
"sns:GetTopicAttributes",
"sns:DeleteTopic",
"sns:TagResource"
],
"Resource": "*"
},
{
"Sid": "IAM",
"Effect": "Allow",
"Action": [
"iam:AttachRolePolicy",
"iam:CreatePolicy",
"iam:CreateRole",
"iam:CreateServiceLinkedRole",
"iam:DeletePolicy",
"iam:DeleteRole",
"iam:DeleteRolePolicy",
"iam:DetachRolePolicy",
"iam:GetPolicy",
"iam:GetRole",
"iam:GetRolePolicy",
"iam:ListPolicyVersions",
"iam:ListRoleTags",
"iam:PassRole",
"iam:PutRolePolicy",
"iam:TagRole",
"iam:UntagRole"
],
"Resource": "*"
},
{
"Sid": "S3",
"Effect": "Allow",
"Action": [
"s3:CreateBucket",
"s3:DeleteBucket",
"s3:DeleteBucketPolicy",
"s3:GetBucketPolicy",
"s3:PutBucketPolicy",
"s3:PutBucketPublicAccessBlock",
"s3:PutBucketTagging",
"s3:PutEncryptionConfiguration",
"s3:PutLifecycleConfiguration",
"s3:PutBucketNotification"
],
"Resource": "*"
},
{
"Sid": "Lambda",
"Effect": "Allow",
"Action": [
"lambda:GetFunction",
"lambda:CreateFunction",
"lambda:DeleteFunctionEventInvokeConfig",
"lambda:DeleteFunction",
"lambda:TagResource",
"lambda:PutFunctionEventInvokeConfig"
],
"Resource": "*"
},
{
"Sid": "S3LambdaCode",
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": "*"
},
{
"Sid": "EventsRule",
"Effect": "Allow",
"Action": [
"events:DeleteRule",
"events:DescribeRule",
"events:PutRule",
"events:PutTargets",
"events:RemoveTargets"
],
"Resource": "*"
},
{
"Sid": "CloudTrail",
"Effect": "Allow",
"Action": [
"cloudtrail:AddTags",
"cloudtrail:CreateTrail",
"cloudtrail:DeleteTrail",
"cloudtrail:StartLogging",
"cloudtrail:PutEventSelectors"
],
"Resource": "*"
},
{
"Sid": "CloudFormation",
"Effect": "Allow",
"Action": [
"cloudformation:GetTemplateSummary",
"cloudformation:CreateStack",
"cloudformation:DescribeStackEvents"
],
"Resource": "*"
}
]
}Run the AWS iam create-policy:
```aws iam create-policy --policy-name Contrast-create-stack --policy-document '{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "CustomResources",
"Effect": "Allow",
"Action": ["sns:Publish"],
"Resource": "*"
},
{
"Sid": "SNS2",
"Effect": "Allow",
"Action": [
"sns:CreateTopic",
"sns:GetTopicAttributes",
"sns:DeleteTopic",
"sns:TagResource"
],
"Resource": "*"
},
{
"Sid": "IAM",
"Effect": "Allow",
"Action": [
"iam:AttachRolePolicy",
"iam:CreatePolicy",
"iam:CreateRole",
"iam:CreateServiceLinkedRole",
"iam:DeletePolicy",
"iam:DeleteRole",
"iam:DeleteRolePolicy",
"iam:DetachRolePolicy",
"iam:GetPolicy",
"iam:GetRole",
"iam:GetRolePolicy",
"iam:ListPolicyVersions",
"iam:ListRoleTags",
"iam:PassRole",
"iam:PutRolePolicy",
"iam:TagRole",
"iam:UntagRole"
],
"Resource": "*"
},
{
"Sid": "S3",
"Effect": "Allow",
"Action": [
"s3:CreateBucket",
"s3:DeleteBucket",
"s3:DeleteBucketPolicy",
"s3:GetBucketPolicy",
"s3:PutBucketPolicy",
"s3:PutBucketPublicAccessBlock",
"s3:PutBucketTagging",
"s3:PutEncryptionConfiguration",
"s3:PutLifecycleConfiguration",
"s3:PutBucketNotification"
],
"Resource": "*"
},
{
"Sid": "Lambda",
"Effect": "Allow",
"Action": [
"lambda:GetFunction",
"lambda:CreateFunction",
"lambda:DeleteFunctionEventInvokeConfig",
"lambda:DeleteFunction",
"lambda:TagResource",
"lambda:PutFunctionEventInvokeConfig"
],
"Resource": "*"
},
{
"Sid": "S3LambdaCode",
"Effect": "Allow",
"Action": ["s3:GetObject"],
"Resource": "*"
},
{
"Sid": "EventsRule",
"Effect": "Allow",
"Action": [
"events:DeleteRule",
"events:DescribeRule",
"events:PutRule",
"events:PutTargets",
"events:RemoveTargets"
],
"Resource": "*"
},
{
"Sid": "CloudTrail",
"Effect": "Allow",
"Action": [
"cloudtrail:AddTags",
"cloudtrail:CreateTrail",
"cloudtrail:DeleteTrail",
"cloudtrail:StartLogging",
"cloudtrail:PutEventSelectors"
],
"Resource": "*"
},
{
"Sid": "CloudFormation",
"Effect": "Allow",
"Action": [
"cloudformation:GetTemplateSummary",
"cloudformation:CreateStack",
"cloudformation:DescribeStackEvents"
],
"Resource": "*"
}
]
}```And obtain a response:
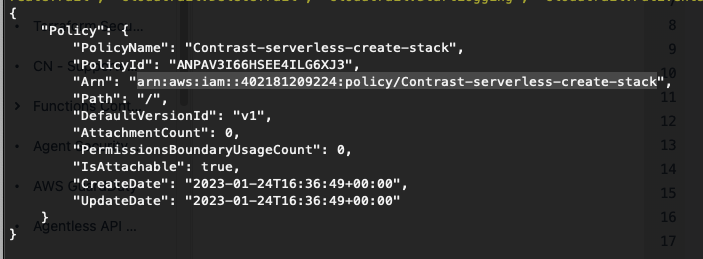
Then attach a user policy:
aws iam attach-user-policy --policy-arn arn:aws:iam::402181209224:policy/Contrast-serverless-create-stack --user-name <USER-NAME></USER-NAME>
And obtain a response:
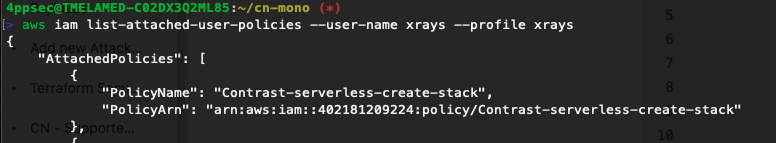
You can now run a deployment.