SCA
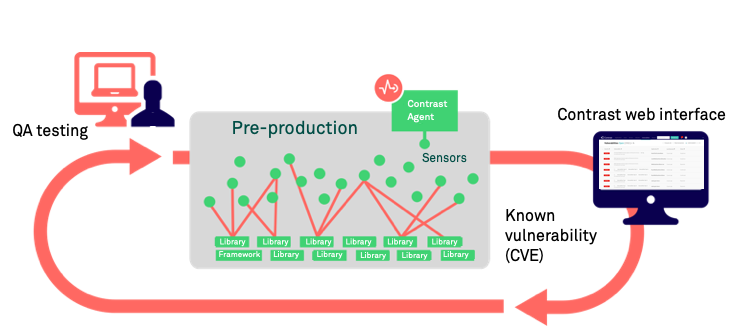
Contrast's Software Composition Analysis (SCA) identifies open-source components through run-time analysis, file system scanning, and dependency analysis. Leveraging these techniques, SCA reports an exact inventory to Contrast.
By default, Contrast Assess includes powerful SCA capabilities. With an SCA license, you have access to advanced SCA capabilities.
Features
To simplify the process and merge open-source analysis with custom code analysis, SCA is integrated as part of the Contrast platform. Here's what you can do with SCA (some of these features are free and other require an SCA license):
Open-source license management: Contrast SCA provides license data tied to open-source components. This data helps you understand intellectual property compliance and mitigate operational risk.
This feature requires an SCA license.
Open-source policy: With SCA, you can set policies to denylist open-source licenses. If a denylisted license type is deployed in your applications, it triggers an alert. To keep your library usage safe, set compliance policies for your organization. To restrict use of specific open-source libraries and licenses, as well as set version requirements, you can set library policies.
This feature requires an SCA license.
Identification of CVE vulnerabilities Contrast SCA identifies the CVE vulnerabilities for each library that your applications are using. This data includes a description of each CVE vulnerability for a selected library as well as the number of applications using that library.
This feature is available without an SCA license.
CLI and dependency tree: The Contrast CLI performs software composition analysis (SCA) on your application to show you the dependencies between open source libraries, including where vulnerabilities were introduced.
The data that the Contrast CLI collects is used to display a dependency tree that brings awareness to underlying library dependencies.
This feature is available without an SCA license.
GitHub action: Use this integration to analyze a project's dependencies for vulnerabilities. The action will run Contrast SCA Action to detect vulnerable libraries. See Contrast SCA Action for more information.
Repository scans: Connect a repository to Contrast to scan for vulnerabilities.
Contrast data
Once a library is reported to Contrast, you can access:
Library usage analysis to identify whether vulnerable components are actually used by the application
Library version identification and guidance on the latest version
Comprehensive vulnerabilities coverage
Portfolio wide, real-time reporting of open-source components
Static SCA
As of June 2024, Static SCA is an opt-in feature. Contrast will support current users by resolving reported bugs.