Attestation reports
Attestation reports provide evidence of vulnerability remediation based on the most current application information. Meet compliance and auditing requirements with these PDF reports.
As of November 7, 2023, this report replaces the Security standards report. The Attestation report provides similar information as the Security standards report. It will help you meet compliance requirements and Identify areas of urgent attention.
Note
This report expires seven days after you create it. Contrast deletes the report after this time.
Attestation reports include:
An itemized list of the specific filter settings used to run the report
A summary of the security posture for the application
Vulnerabilities assessment for both custom code and open-source libraries. Note that critical severities will not be displayed in this section if CVSS 3.1 has not been turned on for existing organizations. To enable this, contact Contrast Support.
Route coverage as a security assessment metric
An optional compliance policy assessment and detailed information about open vulnerabilities for the application
An appendix that describes methodologies and terminologies
Before you begin
An Attestation report has the following limits:
1,350 vulnerabilities with details
18,000 vulnerabilities without details
15,000 routes with observations
30,000 routes without observations
If your report exceeds these limits, an error message displays and the report doesn't generate. If this situation occurs, change your report selections to reduce the amount of information in the report.
Steps to generate an Attestation report
Select Applications in the header.
Select an application in the Applications grid.
Select the Reports icon (
) located at the top-right of the application's page.
Select Generate Attestation Report from the list.
In the Attestation report window, select the Vulnerabilities, Environments, and additional Security Standards that you want to include in the report.
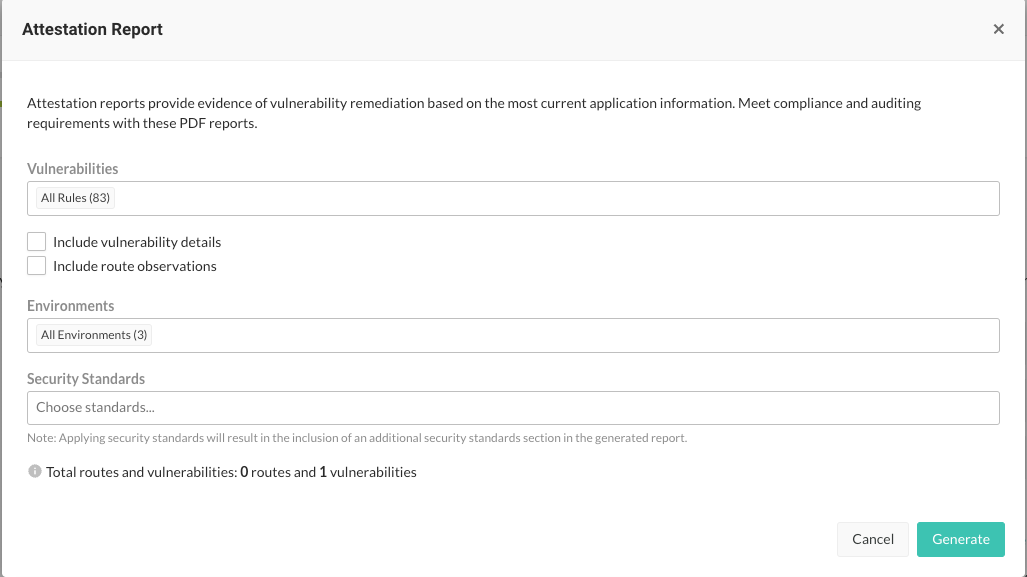
The default is to show all vulnerabilities and environments, but you can filter them by selecting the fields and then, selecting filters. Choose an option from Security Standards to include an additional Security Standards section in the generated report.
Optionally, you can choose to include detailed information about open vulnerabilities and observed routes.
The following table includes the categories that you can use to create a custom report.
Category
Default
Filter options
Vulnerabilities
All
Status (Reported, Suspicious, Confirmed, Not a Problem, Remediated, Fixed, Remediated - Auto-Verified)
Severity (Note, Low, Medium, High Critical)
Assess Rules
Vulnerability details
None
Include vulnerability details by selecting the checkbox for it.
Route observations
None
Include details about observed routes by selecting the checkbox for it.
Environments
All
Development
QA
Production
Security Standards
None
DISA ASD STIG
IPA-7.0
OWASP 2013 Top 10
OWASP 2017 Top 10
OWASP 2021 Top 10
OWASP Top 10 API Vulnerabilities 2019
PCI DSS - 2.0
PCI DSS - 3.0
PCI DSS - 3.2.1
PCI DSS - 4.0
Select Generate.
After Contrast generates the report, the Notifications panel displays a download link for it.
Select the link to download the report.