View application vulnerabilities
From the Applications list, you can view vulnerabilities for a specific application.
Exercise (browse or use) your application so Contrast can find weaknesses and present results in the Contrast application.
To see your application's vulnerability data in more detail, configure your Contrast agent to report session metadata.
Select Applications in the header.
The Applications list displays the number of open vulnerabilities for each application. To view details for specific types of vulnerabilities (for example, critical or high), in the Open Vulnerabilities column, select the relevant section of the bar.
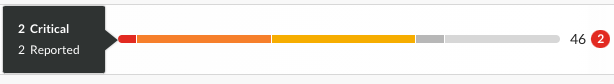
An open vulnerability has a status of Reported, Suspicious, or Confirmed.
Alternatively, In the Applications list, select an application name and then, select the Vulnerabilities tab. You see a list of vulnerabilities for that application.
In the Vulnerabilities tab, to filter vulnerabilities, select the small triangle at the very top of the list.

These filter options are available:
Open
High confidence
Policy violation
Pending review
To search for specific vulnerabilities, select the magnifying glass icon (
 ).
).To view a timeline of the vulnerabilities, select the trend line symbol (
) above the list .
Use the buttons above the chart to view data by Severity or Discovery. Hover over the trend lines to see a breakdown of the data for that point in time (number of vulnerabilities, time stamp, or status).
Any filters you apply in the list also update the data in the chart. Use the filter for the Last detected column to update the time span shown in the timeline.
To filter by columns , select the Filter icon
next to the column headers. These filters are available, if applicable to the selected application:
Severity: Available filters are: Critical, High, Medium, Low, and Note.
Vulnerability: Available filters, if applicable to the selected application, are:
Vulnerability tags : Custom tags you assigned to vulnerabilities
Bugtrackers: Whether you are using bugtracking integrations to track vulnerabilities.
Type: Types of vulnerabilities
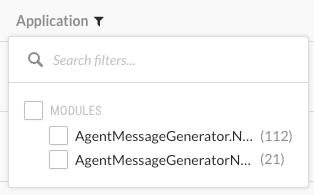
Modules: Application modules associated with a vulnerability, including modules in a merged application.
Servers: Servers hosting the application.
Environments: Development, QA, and production
Sinks: Vulnerabilities that originate from a common sink
A sink is common custom code shared between multiple data-flow vulnerabilities.
Filtering by sink can help you identify a line of code that is causing multiple vulnerabilities.
URLs: Vulnerabilities associated with a specific URL.
Compliance policy: Vulnerabilities associated with selected compliance policies
Routes: Vulnerabilities associated with selected routes.
Application: Modules included in the application.
If you are viewing an unmerged application, this filter shows vulnerabilities for the selected application.
If you are viewing vulnerabilities for a merged application, this filter shows view vulnerabilities for the modules in the merged application.
Last detected: Available filters are: First or Last detected and Time range. Select Custom to enter specific dates and times.
Status: Available filters are Status and whether Contrast is tracking the vulnerability.
Session: This column is visible if you configured session metadata in an agent configuration file but haven't selected a session metadata filter. Use Session column filter to refine the results.
Use the View by menu at the top of the list to filter the data by the session metadata values that you included in your agent configuration file. This filter updates the values shown in the Session column.
The View by menu is visible if you configured session metadata in an agent configuration file but haven't selected a session metadata filter.
Open vulnerabilities for merged applications
For merged applications, the Open Vulnerabilities column in the Applications list displays the number of vulnerabilities for all application modules in the primary application. The Applications list displays the primary application but not the modules in the primary application.
Example:
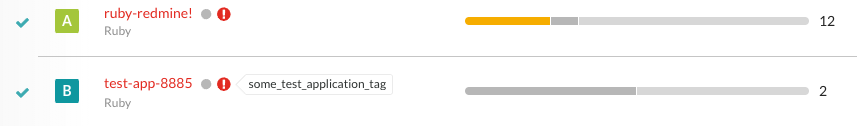
Before you merge applications, the Open Vulnerabilities column looks similar to this:
After you merge applications, the bar in the Open Vulnerabilities column shows vulnerabilities for the primary application and all the merged modules.
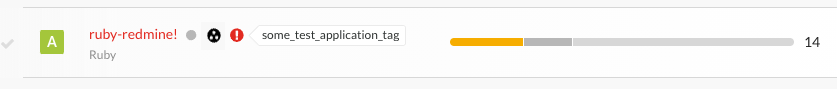
When you view the vulnerabilities tab for a merged application, use the filter for the Application column to view the modules where Contrast found the vulnerability.